1.4 Attacks - Types of Attacks
- Page ID
- 45656
Types of Attacks
In an Information Security context there are 4 broad based categories of attacks:
- Fabrication
- Interception
- Interruption
- Modification
Fabrication
As stated above, fabrication is one of the four broad-based categories used to classify attacks and threats. A fabrication attack creates illegitimate information, processes, communications or other data within a system.
Often, fabricated data is inserted right alongside authentic data. When a known system is compromised, attackers may use fabrication techniques to gain trust, create a false trail, collect data for illicit use, spawn malicious or extraneous processes. In addition, fabricated data may reduce confidence in genuine data with the affected system.
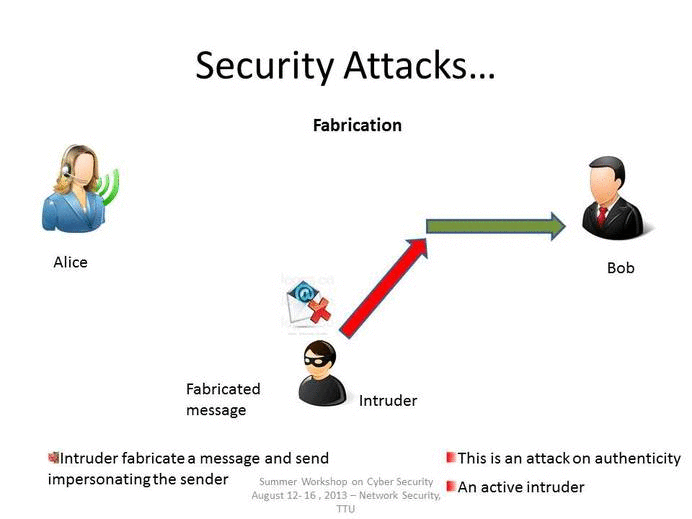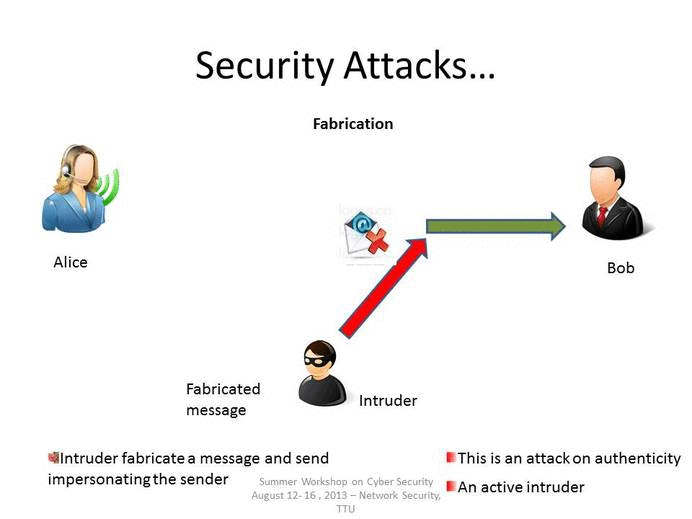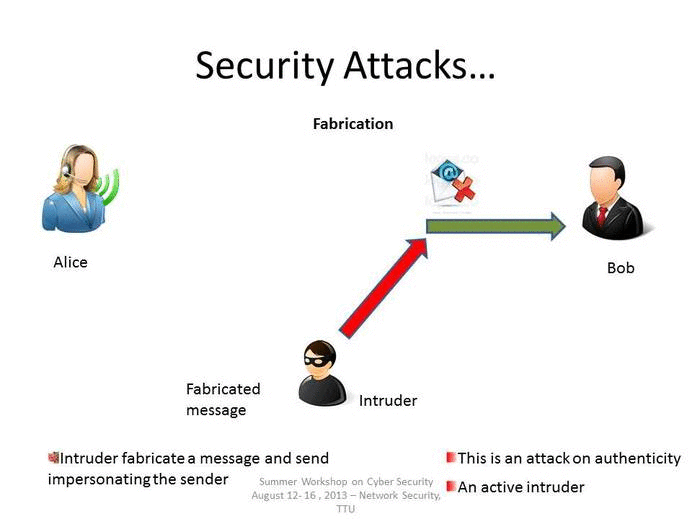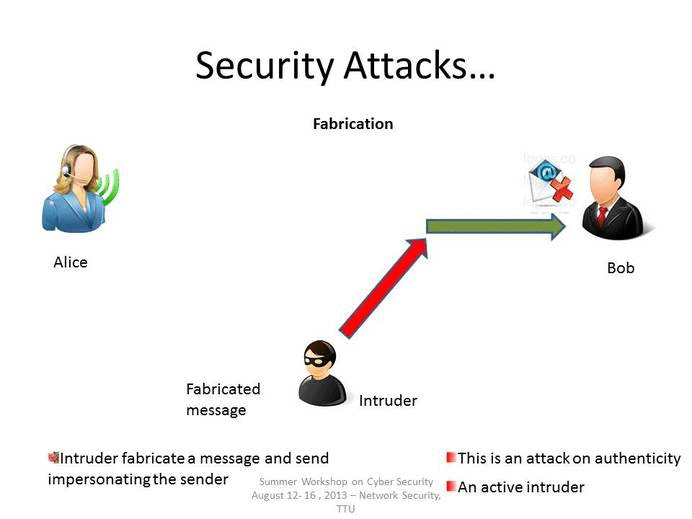
Examples of Fabrication attacks include:
- SQL Injection
- Route Injection
- User / Credential Counterfeiting
- Log / Audit Trail Falsification
- Email Spoofing
Mitigate the attack :
- Use of Authentication and authorization mechanisms
- Using Firewalls
- Use Digital Signatures - Digital signature scheme is a mathematical scheme for demonstrating the authenticity of a digital message or document.
Interception
An interception is where an unauthorized individual gains access to confidential or private information. Interception attacks are attacks against network the confidentiality objective of the CIA Triad.
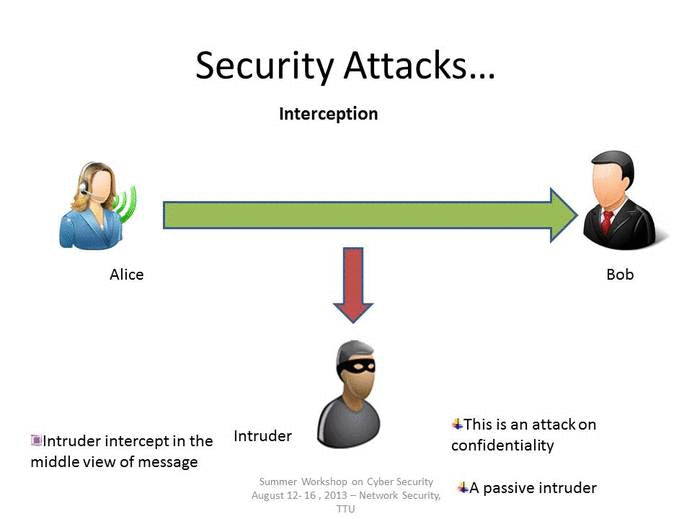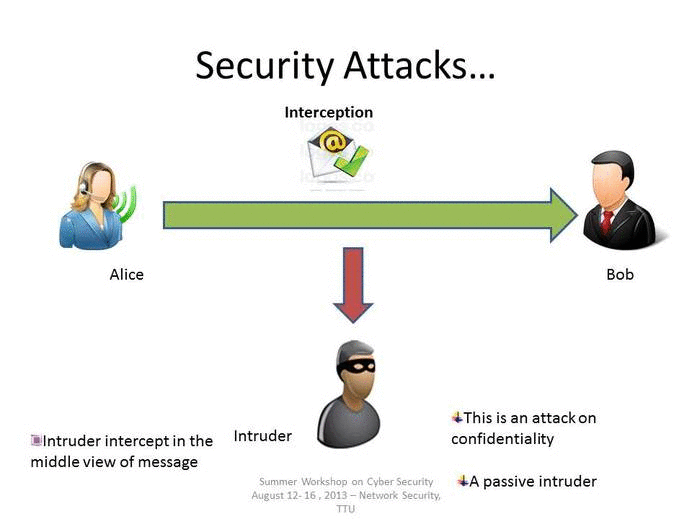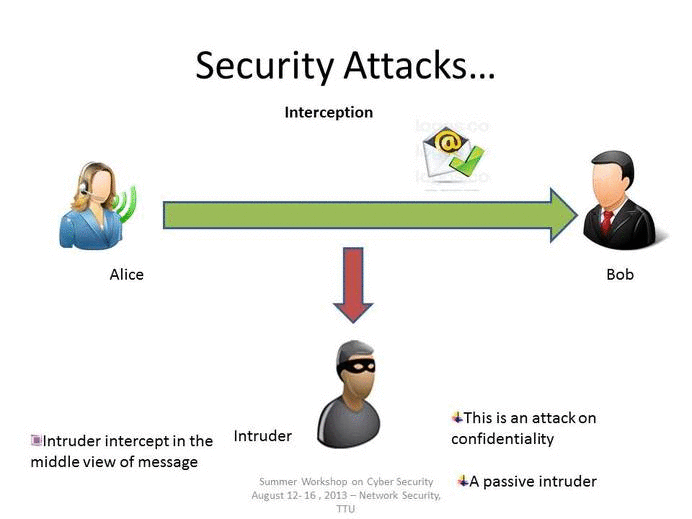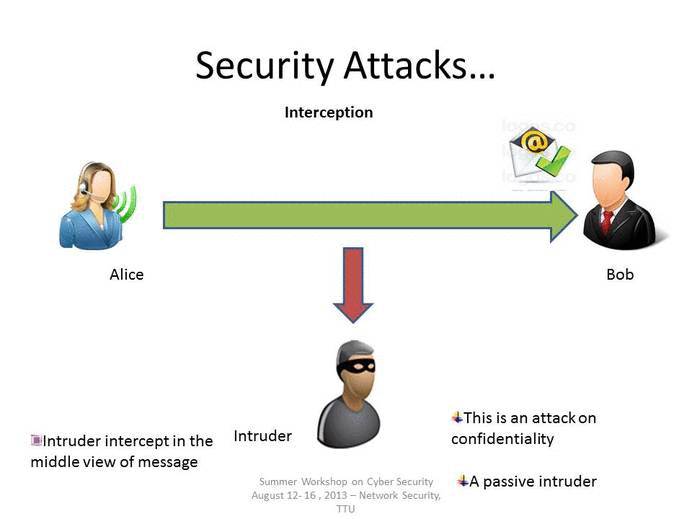
Examples of Interception attacks:
- Eavesdropping on communication.
- Wiretapping telecommunications networks.
- Illicit copying of files or programs.
- Obtaining copies of messages for later replay.
- Packet sniffing and key logging to capture data from a computer system or network.
Mitigate the attack :
- Using Encryption - SSL, VPN, 3DES, BPI+ are deployed to encrypts the flow of information from source to destination so that if someone is able to snoop in on the flow of traffic, all the person will see is ciphered text.
- Traffic Padding - It is a function that produces cipher text output continuously, even in the absence of plain text. A continuous random data stream is generated. When plaintext is available, it is encrypted and transmitted. When input plaintext is not present, the random data are encrypted and transmitted. This makes it impossible for an attacker to distinguish between tree data flow and noise and therefore impossible to deduce the amount of traffic.
Interruption
In an interruption attack, a network service is made degraded or unavailable for legitimate use. They are the attacks against the availability of the network.

Examples of Interruption attacks :
- Overloading a server host so that it cannot respond.
- Cutting a communication line.
- Blocking access to a service by overloading an intermediate network or network device.
- Redirecting requests to invalid destinations.
- Theft or destruction of software or hardware involved.
Mitigate the attack:
- Use Firewalls - Firewalls have simple rules such as to allow or deny protocols, ports or IP addresses. Modern stateful firewalls like Check Point FW1 NGX and Cisco PIX have a built-in capability to differentiate good traffic from DoS attack traffic.
- Keeping backups of system configuration data properly.
- Replication.
Modification
Modification is an attack against the integrity of the information. Basically there is three types of modifications.
- Change: Change existing information. The information is already existed but incorrect. Change attacks can be targeted at sensitive information or public information.
- Insertion: When an insertion attack is made, information that did not previously exist is added. This attack may be mounted against historical information or information that is yet to be acted upon.
- Deletion : Removal of existing information.
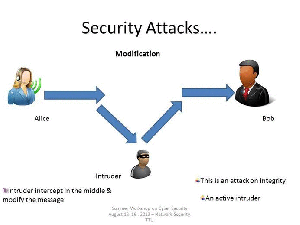
Examples of Modification attacks include:
- Modifying the contents of messages in the network.
- Changing information stored in data files.
- Altering programs so they perform differently.
- Reconfiguring system hardware or network topologies.
Mitigate the attack :
- Introduction of intrusion detection systems (IDS) which could look for different signatures which represent an attack.
- Using Encryption mechanisms
- Traffic padding
- Keeping backups
- Use messaging techniques such as checksums, sequence numbers, digests, authentication codes
Adapted from:
"Network Security" by Unknown, CS Dept - Texas Tech University is licensed under CC BY-SA 4.0


