1.3 Models of Security - CIA / Parkerian Hexad
- Page ID
- 45655
CIA Triad
Information security is not only about securing information from unauthorized access. Information security is basically the practice of preventing unauthorized access, use, disclosure, disruption, modification, inspection, recording or destruction of information. Information can be anything like your profile on social media, your data in mobile phone, your biometrics etc. Thus information security spans so many areas like cryptography, mobile computing, forensics, online social media etc.
Information Security programs are built around 3 objectives, commonly known as CIA – Confidentiality, Integrity, Availability.
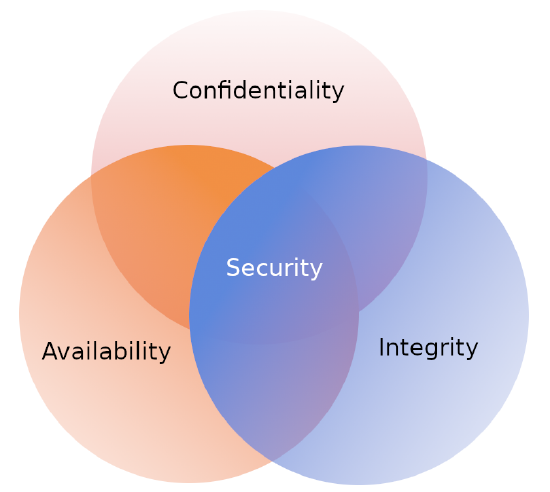
These are the objectives which should be kept in mind while working in the information security realm.
Confidentiality
Confidentiality means that only the authorized individuals/systems can view sensitive or classified information. Data being sent over the network should not be accessed by unauthorized individuals. The attacker may try to capture the data using different tools available on the Internet and gain access to your information. A primary way to avoid this is to use encryption techniques to safeguard your data so that even if the attacker gains access to your data, he/she will not be able to decrypt it. Encryption standards include AES(Advanced Encryption Standard) and DES (Data Encryption Standard). Another way to protect your data is through a VPN tunnel. VPN stands for Virtual Private Network and helps the data to move securely over the network.
Integrity
The next thing to talk about is integrity. Well, the idea here is making sure that data has not been modified. Corruption of data is a failure to maintain data integrity. To check if our data has been modified or not, we make use of a hash function.
We have two common types : SHA (Secure Hash Algorithm) and MD5(Message Direct 5). Now MD5 is a 128-bit hash and SHA is a 160-bit hash if we’re using SHA-1. There are also other SHA methods that we could use like SHA-0, SHA-2, SHA-3.
Let’s assume Host ‘A’ wants to send data to Host ‘B’ maintaining integrity. A hash function will run over the data and produce an arbitrary hash value H1 which is then attached to the data. When Host ‘B’ receives the packet, it runs the same hash function over the data which gives a hash value H2. Now, if H1 = H2, this means that data’s integrity has been maintained and the contents were not modified.
Availability
This means that the data should be readily available to its users. This applies to systems and to networks - not simply the data, but the technology necessary to obtain and view the data need to be available. To ensure availability, the network/system administrator should maintain hardware, make regular upgrades, have a plan for fail-over and prevent bottleneck in a network. Attacks such as DoS or DDoS may render a network unavailable as the resources of the network gets exhausted. The impact may be significant to the companies and users who rely on the network as a business tool. Thus, proper measures should be taken to prevent such attacks.
Along with the 3 objectives that make up the CIA triad, there are 3 additional concepts that are often mentioned in regards to information security. In fact the ISO/IEC 27001, an international standard on how to manage information security, mentions the following concepts as part of an organizations information security management plan. These 3 additional concepts are:
- Non-repudiation – means one party cannot deny receiving a message or a transaction nor can the other party deny sending a message or a transaction. For example in cryptography it is sufficient to show that message matches the digital signature signed with sender’s private key and that sender could have a sent a message and nobody else could have altered it in transit. Data Integrity and Authenticity are pre-requisites for Non repudiation.
- Authenticity – means verifying that users are who they say they are and that each input arriving at destination is from a trusted source.This principle if followed guarantees the valid and genuine message received from a trusted source through a valid transmission. For example if take above example sender sends the message along with digital signature which was generated using the hash value of message and private key. Now at the receiver side this digital signature is decrypted using the public key generating a hash value and message is again hashed to generate the hash value. If the 2 value matches then it is known as valid transmission with the authentic or we say genuine message received at the recipient side
- Accountability – means that it should be possible to trace actions of an entity uniquely to that entity. For example as we discussed in Integrity section Not every employee should be allowed to do changes in other employees data. For this there is a separate department in an organization that is responsible for making such changes and when they receive request for a change then that letter must be signed by higher authority for example Director of college and person that is allotted that change will be able to do change after verifying his bio metrics, thus timestamp with the user(doing changes) details get recorded. Thus we can say if a change goes like this then it will be possible to trace the actions uniquely to an entity.
At the core of information security is information assurance, which means the act of maintaining CIA of information, ensuring that information is not compromised in any way when critical issues arise. These issues are not limited to natural disasters, computer/server malfunctions etc.
Thus, the field of information security has grown and evolved significantly in recent years. It offers many areas for specialization, including securing networks and allied infrastructure, securing applications and databases, security testing, information systems auditing, business continuity planning etc.
Parkerian Hexad
The Parkerian hexad is a set of six elements of information security proposed by Donn B. Parker in 1998. The Parkerian hexad adds three additional attributes to the three classic security attributes of the CIA triad (confidentiality, integrity, availability).
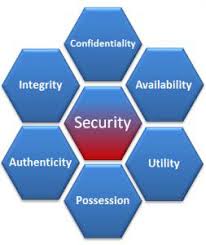
The Parkerian Hexad added the following three additional elements:
Authenticity
Authenticity refers to the veracity of the claim of origin or authorship of the information. For example, one method for verifying the authorship of a hand written document is to compare the handwriting characteristics of the document to a sampling of others which have already been verified. For electronic information, a digital signature could be used to verify the authorship of a digital document using public-key cryptography (could also be used to verify the integrity of the document).
Possession
Possession or control: Suppose a thief were to steal a sealed envelope containing a bank debit card and its personal identification number. Even if the thief did not open that envelope, it's reasonable for the victim to be concerned that the thief could do so at any time. That situation illustrates a loss of control or possession of information but does not involve the breach of confidentiality.
Utility
Utility means usefulness. For example, suppose someone encrypted data on disk to prevent unauthorized access or undetected modifications–and then lost the decryption key: that would be a breach of utility. The data would be confidential, controlled, integral, authentic, and available–they just wouldn't be useful in that form. Similarly, conversion of salary data from one currency into an inappropriate currency would be a breach of utility, as would the storage of data in a format inappropriate for a specific computer architecture; e.g., EBCDIC instead of ASCII or 9-track magnetic tape instead of DVD-ROM. A tabular representation of data substituted for a graph could be described as a breach of utility if the substitution made it more difficult to interpret the data. Utility is often confused with availability because breaches such as those described in these examples may also require time to work around the change in data format or presentation. However, the concept of usefulness is distinct from that of availability.These attributes of information are atomic in that they are not broken down into further constituents; they are non-overlapping in that they refer to unique aspects of information. Any information security breach can be described as affecting one or more of these fundamental attributes of information.
Adapted from:
"What is Information Security?" by rashi_garg, Geeks for Geeks is licensed under CC BY-SA 4.0


