1.6: People and Information Systems
- Page ID
- 95175
People are involved in information systems in just about every way. People imagine information systems, people develop information systems, people support information systems, and, perhaps most importantly, people use information systems. The jobs listed below do not represent all possible jobs within an information systems organization. Larger organizations will have more specialized roles, while smaller organizations may combine some of these roles. Many of these roles may also exist outside of the organization.
Creators
The first group of people to be considered play a role in designing, developing, and building information systems. These people are generally technical and have a background in programming, analysis, information security, or database design. The process of creating information systems will be covered in more detail in Chapter 7.
| Profession | Description of Job Duties |
|---|---|
| Systems Analyst | Manages projects by identifying business needs and imagining a new or redesigned computer-based system to fulfill those needs. |
| Programmer | Writes computer code in a programming language to fulfill the design specifications of the analyst or designer. |
| Computer Engineer | Designs the computing devices that we use every day. Can include software engineers, hardware engineers, systems engineer and network engineers. |
Operations & Administration
Another group of information systems professionals are involved in the day-to-day operations and administration of IT. These people must keep the systems running and up-to-date so that the rest of the organization can make the most effective use of these resources.
| Profession | Description of Job Duties |
|---|---|
| Computer Operator | Oversees the mainframe computers and data centers in organizations. Since mainframe computers increasingly have been replaced with servers, storage management systems, and other platforms, computer operators’ jobs have grown broader and include working with these specialized systems. |
| Database Administrator | Manages the databases for an organization. |
| Help Desk / I.T. Support | First line of support for computer users in a company. |
| Trainer | Conducts classes to teach people specific computer skills |
Managing Information Systems
The management of information-systems functions is critical to the success of information systems within the organization. Here are some of the jobs associated with the management of information systems.
| Profession | Description of Job Duties |
|---|---|
| CIO or CTO | Chief information office (CIO) or chief technology officer (CTO) is the head of the information-systems function. |
| Information Managers | responsible for determining the information needs of the organization, collecting the appropriate data, converting it to information and communicating it. |
| Project Managers | responsible for keeping systems projects on time and on budget. |
| Information Security Officer | in charge of setting information-security policies for an organization, and then overseeing the implementation of those policies. |
Emerging Roles
As technology evolves many new roles are becoming more common as other roles diminish. For example, as we enter the age of “big data,” we are seeing the need for more data analysts and business intelligence specialists. Many companies are now hiring social media experts and mobile technology specialists. The increased use of cloud computing and Virtual Machine (VM) technologies also is increasing demand for expertise in those areas.
Users
Besides the people who work to create, administer, and manage information systems, there is one more extremely important group of people, namely, the users of information systems. This group represents a very large percentage of an organization’s employees. If the user is not able to successfully learn and use an information system, the system is doomed to failure.
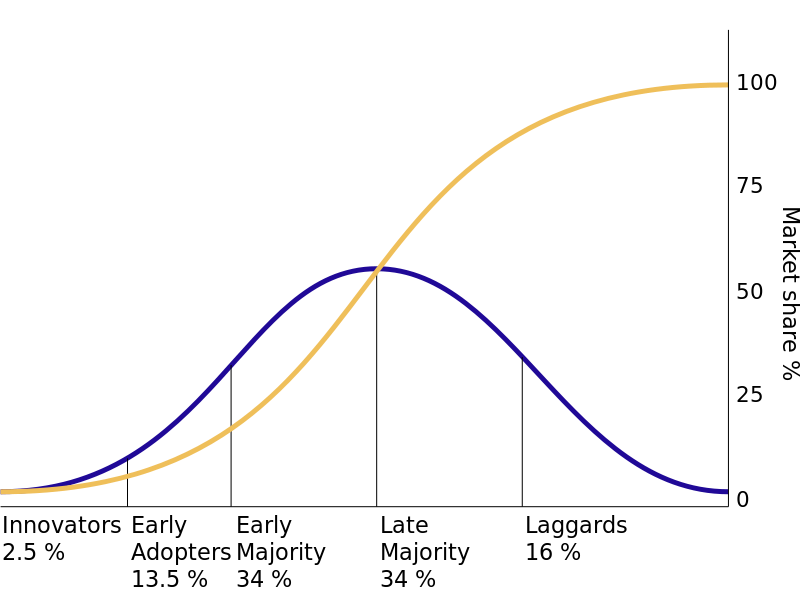
One tool that can be used to understand how users will adopt a new technology comes from a 1962 study by Everett Rogers. In his book, Diffusion of Innovation, Rogers studied how farmers adopted new technologies and noticed that the adoption rate started slowly and then dramatically increased once adoption hit a certain point. He identified five specific types of technology adopters:
- Innovators. Innovators are the first individuals to adopt a new technology. Innovators are willing to take risks, are the youngest in age, have the highest social class, have great financial liquidity, are very social, and have the closest contact with scientific sources and interaction with other innovators. Risk tolerance is high so there is a willingness to adopt technologies that may ultimately fail. Financial resources help absorb these failures (Rogers, 1962, p. 282).
- Early adopters. The early adopters are those who adopt innovation soon after a technology has been introduced and proven. These individuals have the highest degree of opinion leadership among the other adopter categories, which means that these adopters can influence the opinions of the largest majority. Characteristics include being younger in age, having a higher social status, possessing more financial liquidity, having advanced education, and being more socially aware than later adopters. These adopters are more discrete in adoption choices than innovators, and realize judicious choice of adoption will help them maintain a central communication position (Rogers, 1962, p. 283).
- Early majority. Individuals in this category adopt an innovation after a varying degree of time. This time of adoption is significantly longer than the innovators and early adopters. This group tends to be slower in the adoption process, has above average social status, has contact with early adopters, and seldom holds positions of opinion leadership in a system (Rogers, 1962, p. 283).
- Late majority. The late majority will adopt an innovation after the average member of the society. These individuals approach an innovation with a high degree of skepticism, have below average social status, very little financial liquidity, are in contact with others in the late majority and the early majority, and show very little opinion leadership.
- Laggards. Individuals in this category are the last to adopt an innovation. Unlike those in the previous categories, individuals in this category show no opinion leadership. These individuals typically have an aversion to change agents and tend to be advanced in age. Laggards typically tend to be focused on “traditions,” are likely to have the lowest social status and the lowest financial liquidity, be oldest of all other adopters, and be in contact with only family and close friends.
These five types of users can be translated into information technology adopters as well, and provide additional insight into how to implement new information systems within the organization. For example, when rolling out a new system, IT may want to identify the innovators and early adopters within the organization and work with them first, then leverage their adoption to drive the rest of the implementation to the other users. [1]
- Rogers, Everett M. (1962). Diffusion of innovations (1st ed.). New York: Free Press of Glencoe

