15.3: Code Injection
- Page ID
- 19955
If the code to inject is available and can be entered, the next step would be actually getting the code executed.
Based on the previous example call frame, the code would be entered preceded by a series of nop's (0x90). The exact spot where the rip is stored in the stack can be determined through trial and error. When the first byte of the 8 byte address is altered, the program will not be able to return to the calling routine and will likely crash. If the bytes of the rbp are corrupted, the program may fail in some way, but it will be different than the immediate crash caused by the corrupted rip. The code entered would be extended by 1 byte on each of many successive attempts. Finding this exact location in this manner will take patience.
Once the rip location has been determined, the 8 bytes that are entered there will need to be the address of where the injected code is in the stack where the user input was stored. This also would be determined through trial and error. However, the exact address of the start of the injected code is not required. Starting anywhere within the preceding nop's would be sufficient. This is referred to as a NOP slide(For more information, refer to: http://en.Wikipedia.org/wiki/NOP_slide) which will help “slide” the CPU's instruction execution flow to the injected code.
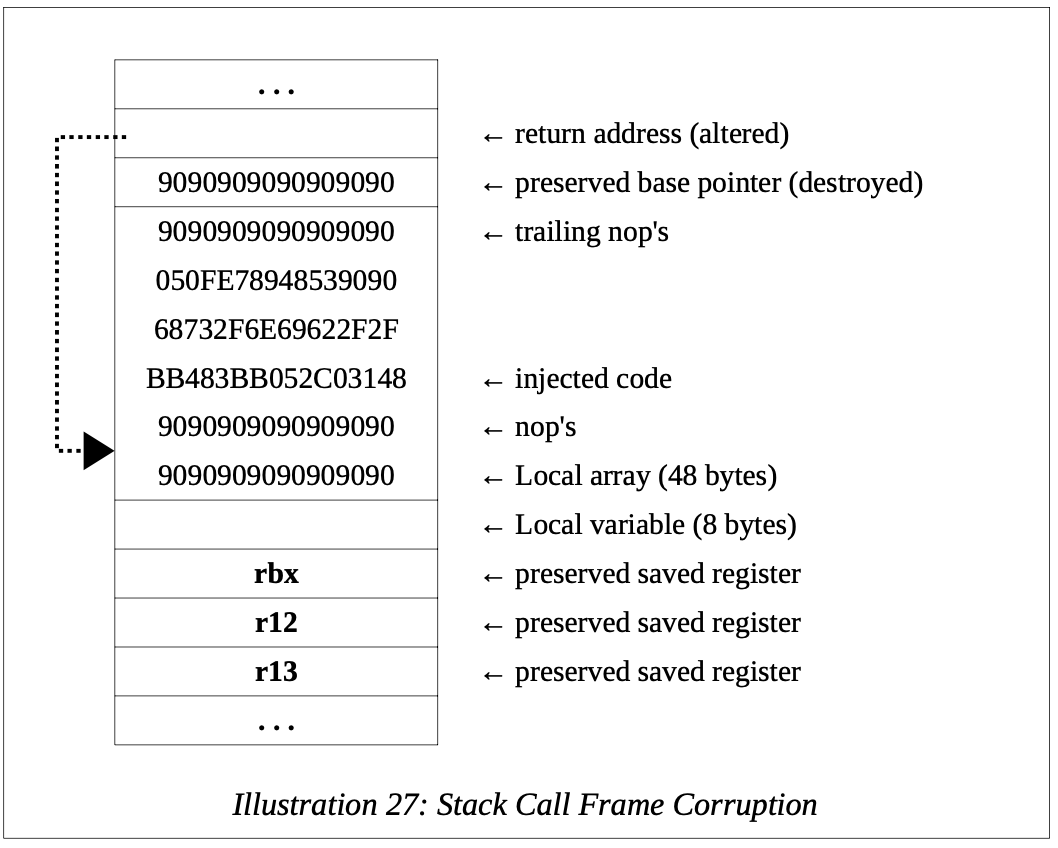
A larger local array would allow even more room for a longer NOP Slide.


