21.4: Appendix D - Quiz Question Answers
- Page ID
- 54596
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\dsum}{\displaystyle\sum\limits} \)
\( \newcommand{\dint}{\displaystyle\int\limits} \)
\( \newcommand{\dlim}{\displaystyle\lim\limits} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\(\newcommand{\longvect}{\overrightarrow}\)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)This appendix provides answers for the quiz questions in each chapter.
24.1 Quiz Question Answers, Chapter 1
There are no quiz questions for Chapter 1.
24.2 Quiz Question Answers, Chapter 2
1) See Section 2.1, Illustration 1, Computer Architecture.
2) Bus or Interconnection.
3) Secondary storage.
4) Primary storage or main memory (RAM).
5) Keeps a copy of the data closer to the CPU, eliminating the extra time required to access the RAM via the Bus.
6) 4 bytes.
7) 1 byte.
8) The LSB is 4016 and the MSB is 0016.
9) The answer is as follows:
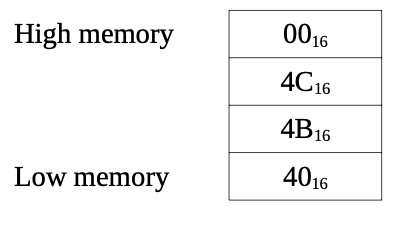
10) The layout is:
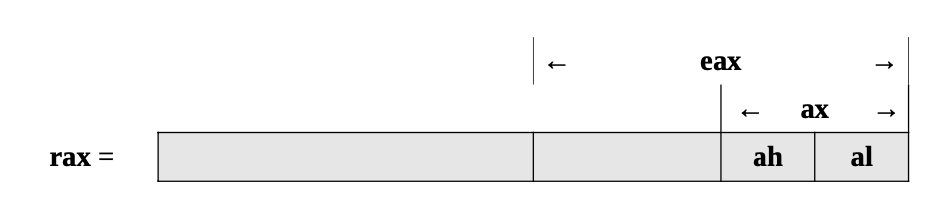
11) The answers are as follows:
- 8
- 64
- 16
- 32
- 64
- 8
- 8
- 16
12) The rip register.
13) The rsp register.
14) The rax register is: \(0000000000000000_{16}\).
15) The answers are as follows:
1. EF\(_{16}\)
2. CDEF\(_{16}\)
3. 89ABCDEF\(_{16}\)
4. 0123456789ABCDEF\(_{16}\)
24.3 Quiz Question Answers, Chapter 3
1) The answers are as follows:
-
-128 to +127
-
0 to 255
-
−32,768 to +32,767
-
0 to 65,535
-
−2,147,483,648 to +2,147,483,647
-
0 to 4,294,967,295
2) The answers are as follows:
- 5
- 9
- 13
- 21
3) The answers are as follows:
- 0xFD
- 0x0B
- 0xF7
- 0xEB
4) The answers are as follows:
- 0xFFEF
- 0x0011
- 0xFFE1
- 0xFF76
5) The answers are as follows:
- 0xFFFFFFF5
- 0xFFFFFFE5
- 0x00000007
- 0xFFFFFEFB
6) The answers are as follows:
- -5
- -22
- -13
- -8
7) \(0.5_{10}\) is represented as \(0.1_2\)
8) The answers are as follows:
- -12.25
- +12.25
- -6.5
- -7.5
9) The answers are as follows:
- 0x41340000
- 0xC1890000
- 0x41AF0000
- 0xBF400000
10) The answers are as follows:
- 0x41
- 0x61
- 0x30
- 0x38
- 0x09
11) The answers are as follows:
- “World” = 0x57 0x6F 0x72 0x6C 0x64
- “123” = 0x31 0x32 0x33
- “Yes!?” = 0x59 0x65 0x73 0x21 0x 3F
24.4 Quiz Question Answers, Chapter 4
1) yasm
2) With the ; (semicolon).
3) Section data.
4) Section bss.
5) Section text.
6) The answers are as follows:
-
bNum db 10
-
wNum dw 10291
-
dwNum dd 2126010
-
qwNum dq 10000000000
7) The answers are as follows:
-
bArr resb 100
-
wArr resw 3000
-
dwArr resd 200
-
qArr resq 5000
8) The declarations are:
global _start
_start:
24.5 Quiz Question Answers, Chapter 5
1) The relationship is 1:1 (one to one).
2) Creation of symbol table, macro expansion, and evaluation of constant expressions.
3) Final generation of code, create list file if requested, create object file.
4) Combine one or more object files into a single executable, update all relocatable addresses, search user and system libraries, create cross reference file if requested, and create final executable file.
5) Attempt to open executable file (verifying existence and permissions), read header information, ask operating system to create new process, if successful, read rest of executable file and load into memory (where specified by operating system), and inform operating system when load is completed. Note, the loader does not run the process.
6) Examples might include:
- BUFFSIZE + 1
- MAX + OFFSET
Note, assumes that upper case implies defined constant. Many examples possible.
7) See Section 5.1, Illustration 4, Overview: Assemble, Link, Load.
8) Atrun-time.
9) The symbol name and the symbol address.
24.6 Quiz Question Answers, Chapter 6
1) By typing: ddd <progName>
2) The“-g”option.
3) Executes the program, always starting from the beginning.
4) The continue command continues to the next breakpoint.
5) Via the menu option Status → Registers.
6) The first is the register name, the second is the hex representation of the value, and the third is the decimal representation of the value (excluding some registers such as rip and rsp which are always shown in hex).
7) There are multiple ways to exit the debugger including typing exit in the command window, clicking the x (upper left corner), or using the menu options File → Exit.
8) There are multiple ways to set a breakpoint including double-clicking on the line, typing b <lineNumber>, or typing b <labelName> (if a label exists on the desired line).
9) The debugger command to read commands from a file is; source <fileName>.
10) The green arrow points to the next instruction to be executed.
11) The answers are as follows:
-
x/db &bVar1
-
x/dh &wVar1
-
x/dw &dVar1
-
x/dg &qVar1
-
x/30db &bArr1
-
x/50dh &wArr1
-
x/75dw &dArr1
12) The answers are as follows:
-
x/xb &bVar1
-
x/xh &wVar1
-
x/xw &dVar1
-
x/xg &qVar1
-
x/30xb &bArr1
-
x/50xh &wArr1
-
x/75xw &dArr1
13) The command is: x/ug $rsp
14) The command is: x/5ug $rsp
24.7 Quiz Question Answers, Chapter 7
1) The answers are as follows:
-
Legal
-
Legal
-
Illegal, 354 does not fit into a byte
-
Legal
-
Illegal, sizes do not match
-
Illegal, cannot change the value 54
-
Legal
-
Legal, while legal it would probably result in an incorrect value
-
Legal
-
Legal
-
Legal, while legal it would probably result in an incorrect value
-
Illegal, cannot move memory to memory
-
Illegal, cannot move memory to memory
-
Legal
-
Illegal, r16 is not a valid register
-
Legal
2) The answers are as follows:
-
Copies the byte value at bVar1 into the rsi register treating as an unsigned value thus setting the upper 56 bits to 0.
-
Copies the byte value at bVar1 into the rsi register treating as a signed value, thus sign extending the upper 56-bits (1's for negative, 0's for positive).
3) The answers are as follows:
-
mov ah, 0
-
cbw
4) The answers are as follows:
-
movzx eax, ax
-
cwde
5) The answers are as follows:
-
mov dx, 0
-
cwd
6) The cwd instruction only converts the signed value in ax into a sign value in dx:ax (and nothing else). The movsx instruction copies the word source operand into the double-word destination operand.
7) On the first instruction, the destination operand size must be explicitly specified since the source operand, an immediate value of 1, does not have an inherent size associated with it. On the second instruction, the destination operand size can be determined from the source operand (since the eax register is a double- word in this case).
8) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 0009
-
rbx = 0x0000 0000 0000 000B
9) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 0007
-
rbx = 0x0000 0000 0000 0002
10) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 0009
-
rbx = 0xFFFF FFFF FFFF FFF9
11) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 000C
-
rdx = 0x0000 0000 0000 0000
12) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 0001
-
rdx = 0x0000 0000 0000 0002
13) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0000 0000 0002
-
rdx = 0x0000 0000 0000 0003
14) The answers are as follows:
-
The destination operand cannot be an immediate value (42).
-
An immediate operand is not allowed since the size/type cannot be determined.
-
The mov instruction does not allow a memory to memory operation.
-
An address requires 64-bits which will not fit into the ax register.
15) The idiv instruction will divide by edx:eax and edx was not set.
16) The operands for the divide a signed (-500), but an unsigned divide is used.
17) The word divide used will place the result in the dx:ax registers, but the eax register is used to obtain the result.
18) The three-operand multiply instructions are only allowed for a limited set of signed multiplication operations.
24.8 Quiz Question Answers, Chapter 8
1) The first instruction places the value from qVar1 into the rdx register. The second instruction places the address of qVar1 into the rdx register.
2) The answers are as follows:
-
Immediate
-
Memory
-
Immediate
-
Illegal, destination operand cannot be an immediate value
-
Register
-
Memory
-
Memory
-
Illegal, source and destination operands not the same size.
3) The answers are as follows (grouped in sets of 4 for clarity):
1. eax = 0x0000 000A
4) The answers are as follows (grouped in sets of 4 for clarity):
-
eax = 0x0000 0003
-
edx = 0x0000 0002
5) The answers are as follows (grouped in sets of 4 for clarity):
-
eax = 0x0000 0009
-
ebx = 0x0000 0002
-
rcx = 0x0000 0000 0000 0000
-
rsi = 0x0000 0000 0000 000C
6) The answers are as follows (grouped in sets of 4 for clarity):
-
rax = 0x0000 0010
-
rcx = 0x0000 0000 0000 0000
-
edx = 0x0000 0000
-
rsi = 0x0000 0000 0000 0004
7) The answers are as follows (grouped in sets of 4 for clarity):
-
eax = 0x0000 0002
-
rcx = 0x0000 0000 0000 0000
-
edx = 0x0000 0005
-
rsi = 0x0000 0000 0000 0003
8) The answers are as follows (grouped in sets of 4 for clarity):
- eax = 0x0000 0018
- edx = 0x0000 0000
- rcx = 0x0000 0000 0000 0000
- rsi = 0x0000 0000 0000 0005
Quiz Question Answers, Chapter 9
1) Therspregister.
2) First, rsp = rsp - 8 and then rax register is copied to [rsp] (in that order).
3) 8 bytes.
4) The answers are as follows (grouped in sets of 4 for clarity):
-
r10 = 0x0000 0000 0000 0003
-
r11 = 0x0000 0000 0000 0002
-
r12 = 0x0000 0000 0000 0001
5) The array is reversed in memory.
6) Memory is used more efficiently.
24.10 Quiz Question Answers, Chapter 10
1) An unambiguous, ordered sequence of steps involved in solving a problem.
2) The answer is as follows:
- Understand the Problem
- Create the Algorithm
- Implement the Program
- Test/Debug the Program
3) No, the steps are applicable to any language or complex problem (even beyond programming).
4) An assemble-time error.
5) An assemble-time error.
6) An assemble-time error.
7) A run-time error.
24.11 Quiz Question Answers, Chapter 11
1) At the top (above the data, BSS, and text sections).
2) Once for each time the macro is invoked.
3) The %% will ensure that a unique label name is generated each time the macrois used.
4) If the %% is omitted on a label, the label will be copied, asis, and thus appear to be duplicated.
5) Yes. This might be used to exit a macro to an error handling code block (not within the macro).
6) The macro argument substitution occurs at assemble-time.
24.12 Quiz Question Answers, Chapter 12
1) Linkage and Argument Transmission.
2) The call and the ret instructions.
3) Call-by-value.
4) Call-by-reference.
5) Once, regardless of how many times it is called.
6) The current rip is placed on the stack and the rip is changed to the address of called function.
7) Save and restore the contents of the callee preserved registers.
8) In: rdi, rsi, rdx, rcx, r8, and r9.
9) In: edi, esi, edx, ecx, r8d, and r9d.
10) That a function may change the value in the register without needing to save and restore it.
11) Two of: rax, rcx, rdx, rsi, rdi, r8, r9, r10, and r11.
12) Call frame, function call frame, or activation record.
13) A leaf function does not call other functions.
14) Clear the passed arguments off the stack.
15) Twenty-four (24) since three arguments at 8 bytes each (8 x 3).
16) The offset is [rbp+16] regardless of which saved registers are pushed.
17) Available memory.
18) Call-by-reference.
19) The 7th argument is at [rbp+16] and the 8th argument is at [rbp+24].
20) Memory efficiency since stack dynamic local variables only use memory when needed (when the function is being executed).
24.13 Quiz Question Answers, Chapter 13
1) The rax register.
2) The operating system.
3) The call code is SYS_write (1). The \(1^{st}\) argument in rdi is the output location STDOUT, the \(2^{nd}\) argument in rsi is the starting address of the characters to output, and the \(3^{rd}\) argument in rdx is the number of characters to write.
4) It is unknown how many characters will be entered.
5) The rax register will contain the file descriptor.
6) The rax register will contain an error code.
7) In: rdi, rsi, rdx, r10, r8, and r9.
24.14 Quiz Question Answers, Chapter 14
1) The statement is: extern func1, func2
2) The statement is: extern func1, func2
3) The assembler will generate an error.
4) Link-time.
5) The linker will generate an unsatisfied external reference error.
6) Yes. However, in the debugger, the code would not be displayed.
24.15 Quiz Question Answers, Chapter 15
1) The buffer overflow exploit is typically called stack smashing.
2) The C function does not check the array bounds of the input arguments.
3) Yes.
4) Typing a very large number of characters when input is requested and, if the program crashes.
5) A series of nop instructions designed to make the target of a buffer overflow exploit easier to hit.
6) Many possible answers. Delete a file, open a network connection, kill a process, etc.
7) Use of canaries, implementation of Data Execution Prevention (DEP), and use of Data Address Space Layout Randomization.
24.16 Quiz Question Answers, Chapter 16
1) The operating system. Specifically, the loader.
2) The program being executed.
3) The name of the executable file.
4) The argc refers to argument count and argv refers to the argument vector (starting address of the table of addresses for the string representing each argument).
5) In the rdi register.
6) In the rsi register.
7) The spaces are removed by the operating system so the program does not have to do anything.
8) No. The program is required to check and determine if that is an error.
24.17 Quiz Question Answers, Chapter 17
1) The end of line character for Linux is linefeed (LF) and the end of line character for Windows is carriage return, line feed (CR, LF).
2) Store a subset of the information for quick access.
3) They are in the language I/O library functions (i.e., cout, cin, etc.).
4) Simplify the programming.
5) I/O performance improvement.
6) The system service functions require a specific number of characters to read which is not known ahead of time for “one line” of text.
7) Keeps a subset of the information at the next higher level in the hierarchy (which is faster than the next lower level).
8) Reduces the overhead associated bus contention and memory latency for excessive system reads.
9) The variable values must be retained between function calls.
10) The end of file must be inferred from the number of characters actually read.
11) Many reasons possible, including file being deleted in another Window after the open or the drive (USB) being removed after the open.
12) The actual number of characters read will be 0 which must be checked explicitly.
13) To ensure the passed line buffer array is not overwritten.
14) By initializing the variables to indicate that all buffer characters have been read.
24.18 Quiz Question Answers, Chapter 18
1) The registers are: xmm0, xmm1, xmm2, . . ., xmm15.
2) Single precision is 32-bit and double precision is 64-bits.
3) Cumulative rounding error associated with the inexact representation of 0.1 in binary.
4) Float functions return the value in xmm0.
5) None of the floating-point registers are preserved.
24.19 Quiz Question Answers, Chapter 19
1) Concurrency implies multiple different (not necessarily related) processes simultaneously making progress. Parallel processing implies that processes are executing simultaneously.
2) Distributed computing and multiprocessing.
3) On different computers connected via a network.
4) Many possible answers, including Folding@Home and SETI@Home. An Internet search can provide a more complete listing.
5) On different cores in the CPU.
6) Distributed computing allows a very large number of compute nodes but requires communications over a network which has inherent communication delays.
7) Multiprocessing allows very fast communications between processes via shared memory but supports only a limited amount of simultaneous executing threads related to the number of cores available.
8) Multiple threads simultaneously writing to a shared variable with no control or coordination.
9) No. No problem exists since the variable is not being changed.
10) Yes. Since the variable is being changed, one thread may alter the value after the other has obtained the value.
24.20 Quiz Question Answers, Chapter 20
1) The operating system is responsible for managing the resources. The resources include CPU cores, primary memory, secondary storage, display screen, keyboard, and mouse.
2) An event that alters the sequence of instructions executed by a processor.
3) An interrupt that is caused by the current process and needs attention of the kernel.
4) An ISR is an Interrupt Service Routine which is executed when an interrupt occurs to service (perform required actions) that interrupt.
5) Interrupt Descriptor Table (IDT) which contains the addresses of the Interrupt Service Routines (ISRs) and the gate information.
6) The interrupt number is multiplied by 16.
7) The ret instruction will pop the return address from the stack and place it in the rip register. The iret instruction will pop the return address and the preserved flag register contents from the stack and place it in the rip register and rFlag registers.
8) The call requires the target address. Since the ISR addresses may change due to hardware changes or software updates, the interrupt mechanism performs a run- time look up for the ISR address.
9) That the interrupt timing, when or even if the interrupt might occur, cannot be predicted in the context of the executing code.
10) That the interrupt timing can be predicted in the context of the executing code. This is typical of system service calls or exceptions such as division by 0.
11) Each instruction changes the rFlag register. After the interrupt is completed, the flag register must be restored to its original value to ensure that the interrupted process is able to resume.
12) Many possible answers, including I/O devices such as keyboard and mouse, network adapter, secondary storage devices, or other peripherals.
13) Many possible answers, including dividing by 0.
14) A maskable interrupt may be ignored briefly where a non-maskable interrupt must be handled immediately.

