1.4.1: Risk and Vulnerabilities
- Page ID
- 45756
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Risks and Vulnerabilities
As an Officer, a leader and manager, one of your jobs will be to assess and manage risk; fortunately you have been managing risk your entire life and continue to do so each day. All we are doing here is honing your risk management skills with a more formalized process and applying that process to the Cyber Domain.
Learning Outcomes
After completing this discussion and the activities you should be able to:
- Explain what a formalized risk assessment process supports/allows
- Describe the general steps of a risk assessment process
- Explain the factors of assessing risks
- Apply the risk assessment process to cyber domain scenarios
Introduction
You assess and manage risk on a daily basis, and you have been doing so your entire life. Why do we look both ways before we walk across a road? Because there is a risk of being hit by a car. The impact of a pedestrian being hit by a car is high (serious injury or death) so we mitigate (reduce) the risk of being hit by looking both ways before we cross the road. Just as in the physical world, there are threats in the cyberspace.
Terminology
- risk
- A measure of the extent to which an entity is threatened by a potential circumstance or event.
- impact
- An adverse effect that results from an event occurring.
- vulnerability
- A weakness in a system that can be exploited by a threat that adversely affects the system, results in an adverse impact. [general context]
- A weakness in an information system that can be exploited to compromise a pillar of cyber security. [cyber domain context]
- threat
- An actor or event with the potential to adversely impact an information system.
- capability
- The knowledge and skill set required by a threat to carry out an event.
- opportunity
- The resources and positioning required by a threat to carry out an action.
- intent
- The motivation of a threat to carry out an action.
The Risk Management Tradeoff
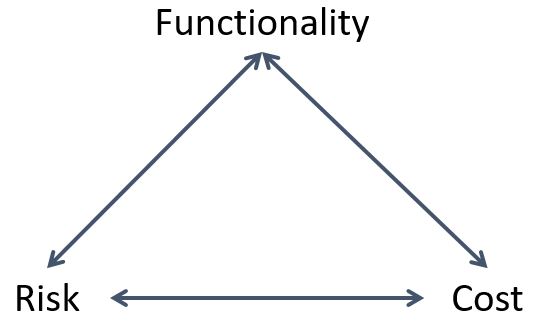
There is a fundamental tension between the services an information system provides (functionality), and security. A building with no doors or windows is quite secure, but pretty limited in its utility. Similarly, an information system with no way for data to flow in or out is very secure, but it is unable to provide a service. The more services you provide/allow, the more ways in and out of your system that need securing. Thus, for each service one needs to weigh the value of the service against the security implications of providing/allowing it. We weigh the risk against the functionality (benefits) and cost to make a decision on how to proceed.
Often times there is no one right answer as to whether a service should be provided/allowed, and the answer is highly situational. The amount of risk that is acceptable for your grandmother's computer is likely different than the computer used by the Chief of Naval Operations (CNO).
What process do we need to go through to assess risk? What are the factors we need to consider? You already have an intuition of what many of the important factors are. What are the benefits of providing or using the service? What are the impacts if the service is compromised? What vulnerabilities are there in providing or using the service? What threats are working to compromise the service? What are the risks inherent in providing/allowing that service? This requires a better understanding of the factors that comprise risk, and leads to developing a repeatable process to assess risk.
Risk Factors
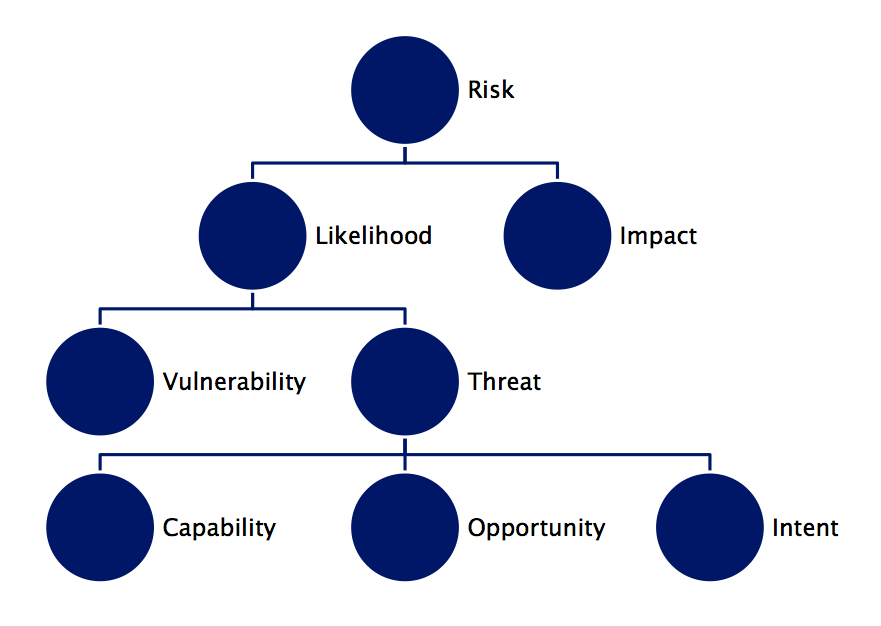
In the cyber domain, just as in all domains, there are various factors that go into assessing risk. Risk Assessment can be viewed as a function with inputs, a process, and outputs. In general risk is viewed as a function of likelihood of occurrence of an event and impact of an event, risk( likelihood, impact ).
Intuitively, if we increase the likelihood of a negative event occurring, the risk severity increases, and vice versa. This is also the case with impact, if the impact of a negative event occurring increases, the risk severity increases.
Likelihood of Occurrence
Likelihood of occurrence can be decomposed into two main components: threat and vulnerability. Threat is any circumstance or event that has the potential to adversely impact our system. Threat can be adversarial (purposely caused by a person) or non-adversarial (caused by an accident or natural event such as a hurricane). Vulnerability represents a weakness in an information system that can be exploited, often by an adversarial threat actor.
Not all vulnerabilities are equal, there are factors that we can assess a vulnerability with. The risk assessment team will ask and answer questions such as (OWASP):
- (Discoverable) How easy is it for an adversary to discover the vulnerability?
- (Exploitable) How easy is it for an adversary to exploit the vulnerability?
- (Awareness) How well known is the vulnerability?
- (Detectable) How likely is an exploit to be detected?
Just as vulnerabilities, threats are also assessed using various factors. The risk assessment team will ask and answer questions such as (OWASP):
- (Capability) How technically skilled is an adversary?
- (Capability) How much does the adversary know about the target system?
- (Opportunity) Does the adversary have the resources (technology) to exploit a vulnerability?
- (Opportunity) Is the adversary in a position to exploit a vulnerability?
- (Intent) How motivated is an adversary to find and exploit a vulnerability?
- (Intent) Does the actor performing the exploit intend harm?
Impact
Impact assessments focus on the resulting damage if a vulnerability is exploited. A single vulnerability may have multiple impacts within the cyber domain, both technological and non-technological. We can apply concepts from conventional operations such as: deceive, deny, disrupt, degrade, and destroy.
Technical impacts are associated to the Pillars of Cyber Security. For example, if the password file for a web based service is compromised, the Authentication pillar is impacted.
Non-technical impacts are associated with the operations and relationships of an organization:
- (Personnel) To what extent are personnel put in physical danger if the vulnerability is exploited?
- (Equipment) To what extent is equipment put in physical danger if the vulnerability is exploited?
- (Operations) To what extent will the success of operations be endangered?
- (Capabilities) To what extent will the capabilities of the organization be damaged?
- (Reputation) To what extent will the organization's reputation be damaged?
- (Financial) What will the financial damage to the organization be?
The to what extent part of assessing impact is not always simple to quantify or qualify.
Common Vulnerability Scoring System
The National Institute of Standards and Technology (NIST) maintains the National Vulnerability Database (NVD). One of the tools provided with the NVD is the Common Vulnerability Scoring System (CVSS). The CVSS supports cyber domain risk assessment efforts. Example: CVSS – ShellShock
The Risk Management Process
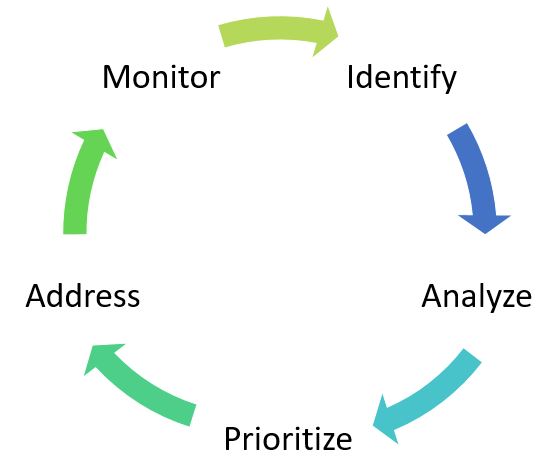
A common first question when presented with a formalized process is: Why is this process necessary?. Following a formalized method allows for the a given process to be repeated; the repeatability allows us to assess process changes and determine if improvement efforts actually achieved the desired results or not. In other words, formalized processes allow us to compare and contrast.
There a number of different methods for assessing risk, most of the methods include a feedback (process improvement) step at the end, making a risk assessment a continual cyclic process. The following are general steps to assessing and managing risk:
Risk assessment begins with identifying risks associated with a task or system. We will use crossing a road as an example. Here are some of the risks associated with crossing a road:
- Identify Risks
Risk assessment begins with identifying risks associated with a task or system. We will use crossing a road as an example. Here are some of the risks associated with crossing a road:
| Risk |
|---|
| Trip and fall |
| Hit by bike |
| Hit by car |
| Fined for jaywalking |
We can look at risk from the viewpoint of the pedestrian or from the driver. In the cyber domain we look at risk from the offensive or defensive viewpoint. In fact, being proficient at assessing and managing risks in the cyber domain requires looking at risks from both an offensive and defensive perspective; a yin and yang.
- Analyze the Risk
Risks are assessed to determine severity based on the event's likelihood and impact. Risks can be assessed using a quantitative (assigned a numeric value) or a qualitative scale (assigned to a category such as low or high). The tables below are extracted from NIST SP800-30 and provide general guidance on how to define likelihood and impact both qualitatively and quantitatively.
Going back to the crossing the road example, we can now assign a qualitative value to each of the risks that were identified in the first step.
| Risk | Likelihood of Occurrence | Impact |
|---|---|---|
| Trip and fall | Low (2) | Very Low (0) |
| Hit by bike | Moderate (5) | Moderate (5) |
| Hit by car | High (8) | High (8) |
| Fined for jaywalking | Low (2) | Very Low (0) |
- Prioritize the Risk
Organizations do not have infinite resources and therefore cannot eliminate or even address all possible risks. Risks must be prioritized by severity so that an appropriate strategy can be developed in line with resource constraints. Generally this just consists of ordering the identified risks from most severe to least severe by assigning quantitative values based on the qualitative values above.
| Priority | Risk | Likelihood of Occurrence | Impact |
|---|---|---|---|
| 1 | Hit by car | High (8) | High (8) |
| 2 | Hit by bike | Moderate (5) | Moderate (5) |
| 3 | Fined for jaywalking | Low (2) | Very Low (0) |
| 4 | Trip and fall | Low (2) | Very Low (0) |
- Address the Risk
Once a risk has been identified, assigned a severity, and prioritized we can determine how the risk will be addressed. There are four strategies for addressing risk:
Note that ignoring risk is not a legitimate strategy. The table below shows our road crossing example with risk strategies applied.
| Priority | Risk | Likelihood of Occurrence | Impact | Strategy |
|---|---|---|---|---|
| 1 | Hit by car | High | High | Control - Look both ways before crossing |
| 2 | Hit by bike | Moderate | Moderate | Control - Look both ways before crossing |
| 3 | Fined for jaywalking | Low | Very Low | Avoid - Only cross at designated crosswalks |
| 4 | Trip and fall | Low | Very Low | Accept |
It is impossible to nullify risk; there is risk in any action. Any risk that remains after a strategy has been applied is known as residual risk. For example, we choose to control our risk of being hit by a car by looking both ways before crossing. While this greatly reduces our risk it does not eliminate it. There is residual risk that a car may suddenly accelerate or take some other unexpected action.
- Monitor the Risk
Risk management is a process. After strategies have been applied to each risk they need to be continually monitored to determine their effectiveness. Questions to ask include:
- Are you using resources effectively?
- Is the risk management strategy working as expected?
- Have any new risks been identified?
- Have any risks changed?
- Have any new threats or vulnerabilities been identified?
- Are new controls available?
If you can answer yes to any of those questions the risk management process should be repeated and results updated. Regardless, the risk management process should be executed on a periodic basis.
Review Questions
1. Why use formalized risk assessments?
2. In your own words, describe each term given pertaining to risk assessments.
3. What is the risk management trade off?
4. What are the general steps of a risk assessment and how can they be applied to cyber?
References
- OWASP. OWASP Risk Rating Methodology. retrieved: 30 Oct 2014.
- Risk Equation
- National Institute for Standards and Technology (NIST) Special Publication 800-30: Guide for Conducting Risk Assessments
Adapted from:
"Risks and Vulnerabilities" by Unknown, U.S. Naval Academy - Cyber Science Dept is in the Public Domain, CC0


