7.3: Network Protocols
- Page ID
- 89395
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\dsum}{\displaystyle\sum\limits} \)
\( \newcommand{\dint}{\displaystyle\int\limits} \)
\( \newcommand{\dlim}{\displaystyle\lim\limits} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\(\newcommand{\longvect}{\overrightarrow}\)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)We already introduced the network security hardware devices so this section will continue address the network software or protocols with respect to security concepts. A network protocol is a set of standardized rules for proper communication between network devices and as mentioned earlier the most common protocol used today is the Transmission Control Protocol/Internet Protocol (TCP/IP).
TCP/IP is not a single protocol but consists of many protocols but the two most important protocols that make up its name are: TCP and IP. TCP is one of the main Transport Layer protocols in Layer 4 of the OSI model; whereas IP is one of the primary protocols that operate at the Network Layer, Layer 3 of the OSI model. There protocols work together because IP is responsible for network addressing and getting the packet on the right path or route to the destination; while TCP is responsible for transmissions control and reliable delivery of the packet.
- Transmission Control Protocol (TCP)
If an application requires reliable data transfer, it uses TCP as the Transport-layer protocol. TCP provides reliability with the following features:- Establishing a connection
- Segmenting large chunks of data
- Ensuring flow control with acknowledgements
Each feature is dependent on the fact that TCP is a connection-based protocol. TCP establishes a connection with the destination, the data is transferred, and the connection is released. A real-world example would be a cellphone call where a user dials a number, a connection is established with a slight delay and if the recipient answers a connection is established and held during the entity of the conversation.
We will not get into the technical details of the TCP header in this chapter but TCP establishes the connection via the TCP Handshaking mechanism which is a three-step process. Each session is assigned a port number to keep track of the numerous numbers of network connections for the applications. Running the network command “netstat” will display the port numbers used and whether or not they are using TCP or UDP as well as private and public IP addresses.
- User Datagram Protocol (UDP)
The other Transport Layer (Layer 4) protocol is UDP. UDP is an alternative protocol that is primarily used for establishing low-latency or loss-tolerating connections between applications on the Internet. UDP enables process-to-process communication by sending “datagrams” and used a “best-effort” delivery method. UDP does not need to establish a connection and thus does not provide flow and error control; therefore, is often referred to as connection-less whereas, TCP is connected-based.UDP also used port numbers to help distinguish different user requests and optionally offers a checksum to verify that data does arrive intact. A big difference between UDP and TCP is that packets may take different paths between the sender and receiver so some packets may be lost or may be received out of order.
UDP is an ideal protocol for network applications in which perceived latency is critical such as in gaming, voice and video communications which can suffers some data loss without affecting overall quality.
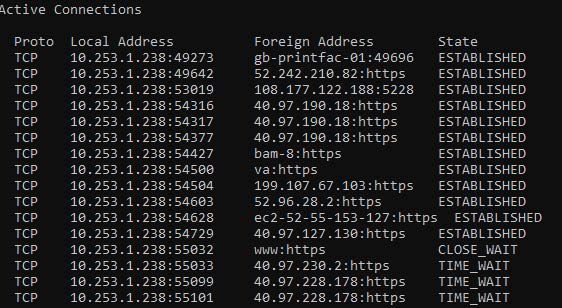
Figure \(\PageIndex{1}\): TCP Traffic ("Information Security" by Umar Khokhar Binh Tran, OpenALG is licensed under CC BY 4.0)
- Domain Name System (DNS)
The Domain Name System (DNS) is a TCP/IP protocol that resolves or maps a Fully Qualified Domain Name such as www.google.com with one of its corresponding IP addresses such as 64.233.177.103. The DNS database is organized in a tree-like hierarchy as shown in figure 2.6: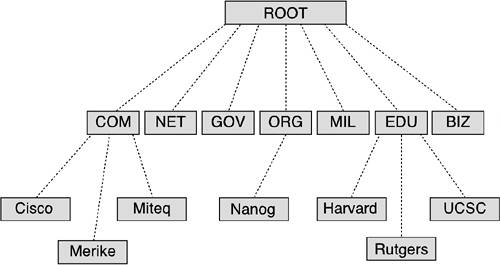
Figure \(\PageIndex{1}\): Copy and Paste Caption here. (Copyright; author via source)
The top-level domains (TLDs) are organized into categories such as commercial (.com), nonprofit organizations (.org), government (.gov), education (.edu) or country of origin represented by a two-letter code such as Canada (.ca). The second-level domains are usually the names the companies or institutions. The host level represents individual computers or servers such as www which hosts all the web files or mail which maintains all the mailboxes.
Local DNS servers can be configured to the local organization websites for example www.company.com but they are also configured to know where the “root” servers are around the world in case they need to resolve addresses that are not in their local database. To help speed up this process some servers and clients make use of the DNS cache which stores the domain names and IP address pairs resolved recently in their local memory.
Because of its importance DNS is often the focus of security attacks. DNS poisoning results in substitute addresses so that the computer is redirected to another device and this can be done by the attacker at either the local host table, or the external DNS server. A variation of DNS poisoning involves replacing a MX (mail exchange) record resulting in all email being sent to the attacker instead of the proper MX server.
Finally, a DNS transfer attack tricks the server into giving information that the attacker could then use to map out the entire internal network of an organization that is linked to the DNS server. This can then be used in many ways to determine weaknesses in the network for other types of attacks.
- Internet Protocol (IP)
The Internet Protocol (IP) is the heart of the TCP/IP protocol suite. IP addresses are defined at the Network Layer (Layer 3) of the OSI model and the Internetwork Layer of the TCP/IP. This is where network routing takes place and without routing the Internet and World Wide Web as a whole would not exist. The Internetwork layer is responsible for several main functions:An IP address is assigned to every computer and network device that uses TCP/IP protocols for communications. The purpose of the IP address is to identify the device at the Internetwork or Network layer and also to identify which network it resides on because there would be many networks or subnetworks in an organization. IP addresses work similar to the 10-digit phone number used in the U.S. where the first three represent the area code and the last seven represent the individual number. Each IP address can be broken down into the Network ID and the Host ID.
The next task is to determine the best path to get the packets from the sender to the receiver navigating all the networks in between them. Similar to the Interstates in the U.S. many large networks have many paths that can be taken to get from one location to another. This “routing” task is shared with all the routers in the world network which must communicate with each other to determine the best path at any particular time.
The network packet that sent or received includes both the physical (MAC) and logical (IP) source and destination addresses so when it gets to the final destination it will know which unique device defined by MAC address needs to get the end information. This task is assisted by another protocol called Address Resolution Protocol (ARP) which maintains a table of MAC addresses and their respective IP addresses.
- Defines and verifies IP addresses
- Routes packets through an internetwork
- Resolves MAC addresses to IP addresses
- Delivers packets efficiently
- Address Resolution Protocol (ARP)
Address Resolution Protocol (ARP) is used to resolve a logical IP address to a physical MAC address. The IP protocol’s purpose to get the packet to the correct network and once in that particular network it can query the ARP cache or table to find the physical address to populate into the Data Link (Layer 2) frame for proper delivery.
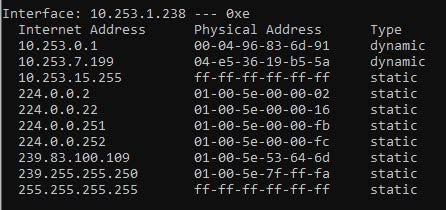
Figure \(\PageIndex{1}\): ARP Cache of the local computer ("Information Security" by Umar Khokhar Binh Tran, OpenALG is licensed under CC BY 4.0)
The process can be very complex and we will not go into its details in this chapter but one of the potential targets for attack is the ARP cache. In an attack called ARP poisoning or spoofing the attacker sends falsified ARP messages over the local area network, and by doing so the results allow the attacker to link their MAC address with the IP address of a victim server or computer on the network.

