8.1.1.3: Cross Site Scripting (XSS)
- Page ID
- 89758
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \) \( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)\(\newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\) \( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\) \( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\) \( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\) \( \newcommand{\Span}{\mathrm{span}}\) \(\newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\) \( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\) \( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\) \( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\) \( \newcommand{\Span}{\mathrm{span}}\)\(\newcommand{\AA}{\unicode[.8,0]{x212B}}\)
XSS attacks are just like injection attacks where the server accepts the untrusted input from the user/attacker and then lets the attacker manipulate the webserver operations.
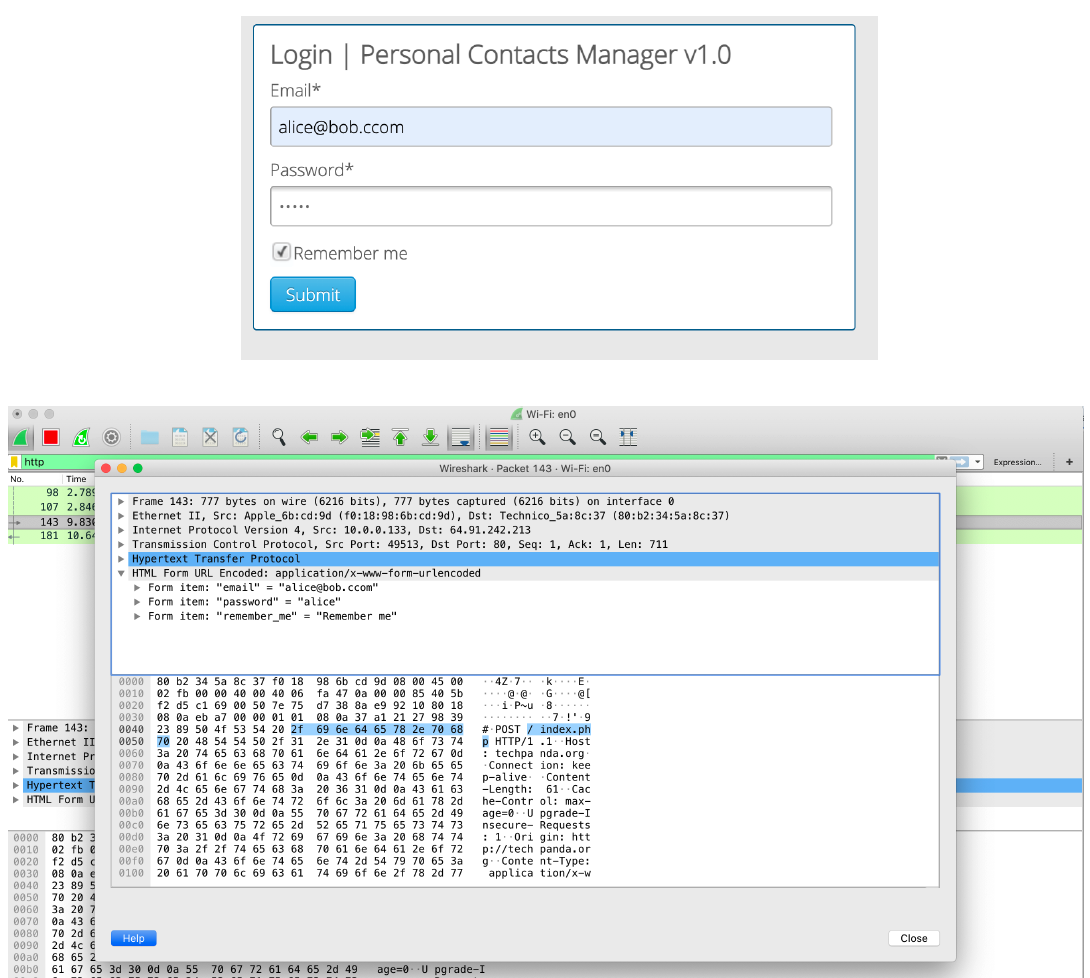
Interception using Wireshark
("Information Security" by Umar Khokhar Binh Tran is licensed under CC BY 4.0)There are two types of the XSS attacks: XSS Reflection and XSS Stored/Persistent:
- XSS Reflection: Firstly, the attacker finds a vulnerable website (which does not validate the user’s input; typically blogging sites) then post a comment on a vulnerable website with underlying malicious script. When any user clicks the comment to respond then it can result in many malicious outcomes e.g.
- Steals the user browser’s history or cookies
- Redirects the users to a crafted/fraudulent website
- Install a malicious software or Add-ons
- XSS Stored/Persistent: The XSS stored is more dangerous as compared to XSS reflection. In a XSS stored attack, the attacker injects the malicious scripts that are stored on vulnerable servers. Then, whoever visits that containment webserver, becomes the victim of the attack e.g. The attacker can store a cookies stealing script on the webserver and then anyone who visits the website, the malicious script forwards a copy of the session cookie to attacker. Figure 8.1 shows the session key stealing script.

