9.3: Types of Active Threats
- Page ID
- 89928
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)The following are the types of different active threats that can exploit the vulnerabilities of the computational systems which eventually compromise the security.
9.3.1 Password Cracking attacks:
Most of the password cracking attacks are offline, where the attacker steals the hash file of the password and use cracking tools to guess the password. Some of the following methods are widely used in cracking tools
- Birthday attack: The birthday attack is a type of cryptographic attack that exploits the mathematics behind the birthday problem of the probability. The birthday problem concerns the probability in a set of ‘n’ people having same birthday. The birthday attack model uses the probability of ‘n’ people having the same password to guess the password.
- Dictionary attacks: Instead of launching brute force (all possible combinations), in this attack model, the attacker does three tasks; create a dictionary of the relevant passwords, calculate the hashes of dictionary and then make a comparison of all computed hashes with stolen hash to guess the password.
- Session Hijacking: The attacker intercepts the communication of server and victim’s computer and steals the session token. After having the session token, the attacker takes the control of session and can inject malicious traffic to both the server and the victim’s computer.
- Social Engineering attack: The attacker tricks the users to get the confidential information by creating a con, sending phishing email or pharming (Section 3.3.3 discusses the Social Engineering attacks are discussed in detail).
9.3.2 Malicious Software
The short form of Malicious Software is Malware where ‘Mal’ is take from Malicious and ‘ware’ is taken from software. Any software which does the following four functions is known as malware;
- Causes the damages
- Bypass the security framework
- Disclose the confidential data
- Modify or delete data
There are many types of malware, some of the common malware types are as follows:
9.3.2.1 Virus
The term computer virus is inspired from its biological counterpart. A biological virus firstly infects one cell then it turns the infected cell into factory of virus and start infecting other cells. Similarly, after entering the computer, the virus attaches itself with a file and starts infecting that file. Then the infected file starts infecting other files and eventually creates obstruction in the normal operation of the computer.
A computer virus can be formally defined as “A small piece of code that migrates through networks and can attach itself with different program files”. The virus cannot replicate itself and it requires a human intervention for transportation. The following are the three main virus infection methods:
- Appender Infection : In this infection method, the virus appends itself at the end of the program file instruction at the beginning of the program code. Whenever the user opens the file, the jump instruction redirects the control to the virus code. The Appender infection virus can be easily detected by the antivirus (while scanning the infected file).
- Swiss Cheese Infection: This infection method is similar to the Appender method, where the virus code attaches itself at the end of the program file. However, the virus code is encrypted which makes it hard to detect for anti malware. The decryption keys are randomly placed across the program file and tied together with jump instructions. When the program file is executed the virus code is unveiled and takes control over the session.
- Split Infection : The virus code is broken down into several small pieces and placed at random locations across the program files. The small chunks of the virus code are tied up through a jump instruction and when the infected file is executed, the control is redirected to virus main body
The figure 9.3 describes the three virus infection methods.
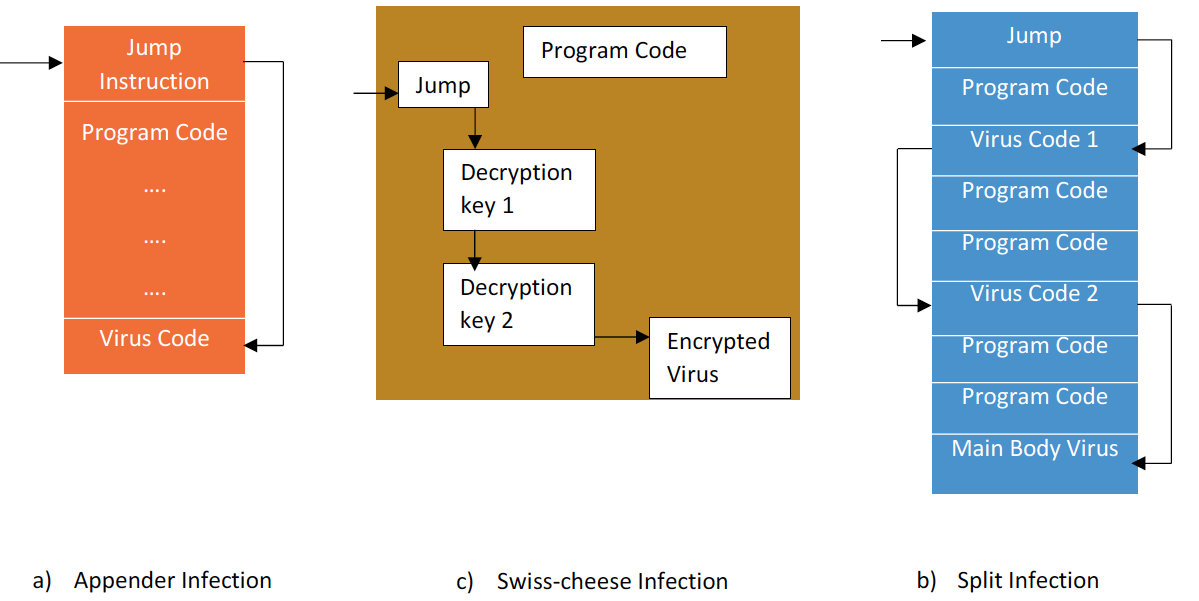
Figure \(\PageIndex{1}\): Virus Infection Methods ("Information Security" by Umar Khokhar Binh Tran is licensed under CC BY 4.0)
9.3.2.2 Worm
The worm is a self-contained program that replicates itself and propagates across computer and network without human intervention. The main objective of the worm is to exhaust the network bandwidth and create botnets.
9.3.2.3 Torjan Horse
The programs that disguised as something useful with underlying malicious contents and backdoors. Usually, the trojan horse arrives with the free downloadable contents or sometimes just by visiting malicious websites. The trojan horse collects and sends the sensitive information of the victim’s computers (which includes web browser history and cookies etc.) to the attackers. Also, trojans open the backdoors (open ports, turn off AVS etc.) to let the bad traffic in, on the victim’s computer.
9.3.2.4 Rootkits
The rootkits hide themselves in Operating System files and get triggered each time whenever the victim restarts (reboot) the computer. The rootkit allows the remote user (attacker) to install the rogue files, delete the files, create backdoor and also rootkits hide the existing malware from being detected as well.
9.3.2.5 Adware
The Advertisement Software (Adware) usually designed using JavaScript and are embedded on the malicious websites. When, the victim visits the malicious website the script automatically runs and installs itself on the victim’s computer. The adware collects the web browser history and then create an unsolicited targeted advertisement and popup messages. The adware can also pull the session and persistent cookies which are serious threat to privacy and security of the individual.
9.3.2.6 Spyware
The spyware collects and forwards the victim’s activities and classified information which includes keystrokes, passwords, web browser history and cookies to the attacker. The keystroke logger is one of the most common type of spyware which records all the keystrokes of the users and sends the recorded data to the attacker.
9.3.3 Social Engineering attacks
The Social Engineering is a process that utilizes the knowledge of the human nature to get information from people which can be further used for destructive purposes. The Social Engineering techniques involves some kind of deception and trick the innocent users to get their classified information (such as passwords, Social security numbers or Financial details). The main idea of the Social Engineering is “Rather than cracking the password why not ask them their password”. The following are some types of the Social Engineering techniques:
- Authority: Use of power/position to get classified information of the subordinates.
- Dumpster Diving: Collection of information from Un-shredded papers.
- Hoax: Creating a con that involves some kind of deception to get the confidential information of people.
- Phishing: Tricking the people over email (Malware can also be attached with emails).
- Vishing: Tricking the people over phone (Impersonation).
- Whaling: Targeting the top-level managers (Executives) of an organization.
- Pharming: The attackers craft a real looking fake website and then try to redirects the users to the fraudulent website to get their confidential information.

