10.1: What is Social Engineering
- Page ID
- 91389
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\dsum}{\displaystyle\sum\limits} \)
\( \newcommand{\dint}{\displaystyle\int\limits} \)
\( \newcommand{\dlim}{\displaystyle\lim\limits} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\(\newcommand{\longvect}{\overrightarrow}\)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)

Social engineering is leveraging social contracts and manipulating people to divulge information or behave in a certain way. Social engineering is hacking humans. Social engineering is conning people.
One of the best known social engineering artists is Kevin Mitnick. Kevin spent five years in jail for a number of computer related crimes. Most of his imprisonment and charges were highly controversial, and Mitnick was seen as an idol in the hacking community. Since his release, he has written four books. His first, The Art of Deception, is the bible of social engineering (you should totally read the book!).
He owns Mitnick Security Consulting, LLC and is also the Chief Hacking Officer and part owner of the security awareness training company KnowBe41. One of the KnowBe4 tools includes sending fake emails to employees at companies to see if they fall for the bait (they also offer cybersecurity training). If you’d like to know more, you can read chapter 3 from the 2012 book The Path of Least Resistance for free.
You should be intimately aware of phishing by now - and phishing falls under the umbrella of social engineering. Consider these real-life cases:
“You gotta send that money NOW!” CEO says
Though his identity remains anonymous (and you’ll see why in a minute), in 2019 the CEO of an unnamed UK energy firm received a phone call from the Chief Executive of the parent company - a person he knew well. He transferred about $240,000 to the account of a Hungarian supplier2. Business as usual. Sure, there was a bit of urgency to the request, but he knew the person requesting the transfer so it didn’t raise any flags. The catch? The CEO of the parent company never made the request and the transferred money was immediately moved to another account (and was lost for good). The culprit? The voice of the CEO was mimicked by artificial intelligence3.
Help the police
In 2021, a 90-year-old woman in Hong Kong was contacted by law enforcement in mainland China. It seemed that someone had been using her identity for criminal activities. The law enforcement agency sent over an officer to deliver a cell phone for direct communication with them. Happily, she was able to rectify the mistaken identity by giving the authorities roughly $32 million dollars… Or did she? Turns out the phone calls and the officer were both part of a scam4.
Out of order
Back in the 1960s it was common for businesses to drop bags of money off at banks after hours; they would deposit the money in a one-way vault at the bank. On one particular night, around thirty people from various companies arrived at the bank to see a sign that said, “NIGHT DEPOSIT VAULT OUT OF ORDER. PLEASE MAKE DEPOSITS WITH SECURITY OFFICER.” Each of the thirty employees did as instructed and received a hand-written receipt from the bank’s security guard. Turns out the security guard was not employed by the bank; he had just obtained a uniform and fabricated the sign.5 Perhaps you’ve heard of the imposter - Frank Abagnale (whose adventures were chronicled in the 2002 movie Catch Me if You Can.
Yes, the name of my company is legit
In 2019 the Department of Justice finally caught up with Evaldas Rimasauskas (a Lithuanian citizen). He discovered the name of a company in Asia that sold products to big tech companies like Facebook and Google and then incorporated a company with the same name in Latvia. After creating a few corporate bank accounts with the same name in Latvia and Cyprus, he started sending invoices to the big tech companies. Over the course of three years, he stole over $100 million!6
Department of Labor invites you to bid on work
In 2022 the Department of Labor sent emails to vendors inviting them to submit bids for upcoming projects. The professional emails had PDFs attached with instructions on how to submit a bid. The PDF had a link to the bidding site, and the site had DoL branding. One of the steps for bidding included a Microsoft Office 365 login (you probably see where this is going). Turns out that the URL for submitting the bids (and the email address) were not genuine DoL addresses. Instead, they were derivatives (like doi-bids.us, for instance).7
Who doesn’t love packages?
In April 2021, people across the country started receiving texts from the United States Postal Service about packages in transit that had been rerouted. All you had to do was click on the link to track the package and see the updates. As you’ve probably guessed, the link led to malware with the intention of stealing some of your data.
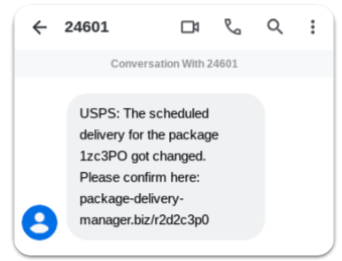
Of course, an astute person would recognize that the link looks wonky, but that didn’t stop people from clicking on it.8
Texts and calls
Later that year, attackers ramped up their methods. A man’s daughter received a text from J.P. Morgan inquiring about a $5000 transaction. She replied “NO” and immediately received a phone call from the bank confirming that the transaction attempt was fraudulent. The catch is that she was asked to verify some account details to make sure she was who she claimed she was. This story has a happy ending; she was savvy enough to tell the caller that she would call the bank herself - using the
official phone number. She avoided a potentially catastrophic attack.9
Social engineering is a serious threat to organizations. In 2021, over 80% of organizations surveyed by Proofpoint reported a successful email phishing attempt (that was up from 46% in 2020!). Proofpoint attributes three factors - “Pandemic Fatigue” (employees are more likely to make an error in their inbox attentiveness), shifting infrastructures (cloud computing and personal devices have been adopted without sufficient training and configuration), and seductive lures in emails (namely Squid Game, Justin Bieber World Tour, and economic issues such as unemployment and relief10).
A report from Stanford found that 47% of respondents have admitted to clicking on links in phishing emails. While this data is insightful, there is concern that it is underreported. Based on other factors in the survey, Stanford suggests that some respondents were unaware that they had engaged with phishing emails. They also hypothesized that people under report for fear of their job.11
Phishing attempts typically result in either compromised data or ransomware victimization. According to Sophos, the average bill for rectifying a ransomware attack in 2021 was $1.85 million.12 Perhaps you remember the Colonial Pipeline ransomware attack - that cost about $5 million (though the FBI was able to recover about half of that after the fact).13 But the trophy for the biggest payout of 2021 (and a new World Record!) goes to CNA Financial Corporation. A payout of $40 million in March of 2021 to a Russian Cybergang.14
- Kevin Mitnick [Wikipedia]
- A Voice Deepfake Was Used To Scam A CEO Out Of $243,000
- Fraudsters Used AI to Mimic CEO’s Voice in Unusual Cybercrime Case
- 90-year-old Hong Kong woman loses $32 million in phone scam
- Catch Me If You Can: The True Story of a Real Fake
- Lithuanian Man Pleads Guilty To Wire Fraud For Theft Of Over $100 Million In Fraudulent Business Email Compromise Scheme
- Office 365 phishing attack impersonates the US Department of Labor
- Don’t click the link: USPS scam texts draw attention to ‘smishing’
- SMS About Bank Fraud as a Pretext for Voice Phishing
- 2022 State of the Phish
- Understand the mistakes that compromise your company's security
- The State of Ransomware 2021 [Sophos]
- U.S. recovers $2.3 million in bitcoin paid in the Colonial Pipeline ransom
- CNA Financial Paid $40 Million in Ransom After March Cyberattack

