9.5: Privacy
- Page ID
- 94945
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)The term privacy has many definitions, but for purposes here, privacy will mean the ability to control information about oneself. The ability to maintain our privacy has eroded substantially in the past decades, due to information systems.
Personally Identifiable Information
Information about a person that can be used to uniquely establish that person’s identify is called personally identifiable information, or PII. This is a broad category that includes information such as:
- Name;
- Social Security Number;
- Date of birth;
- Place of birth;
- Mother‘s maiden name;
- Biometric records (fingerprint, face, etc.);
- Medical records;
- Educational records;
- Financial information; and
- Employment information.
Organizations that collect PII are responsible to protect it. The Department of Commerce recommends that “organizations minimize the use, collection, and retention of PII to what is strictly necessary to accomplish their business purpose and mission.” They go on to state that “the likelihood of harm caused by a breach involving PII is greatly reduced if an organization minimizes the amount of PII it uses, collects, and stores.”[10] Organizations that do not protect PII can face penalties, lawsuits, and loss of business. In the US, most states now have laws in place requiring organizations that have had security breaches related to PII to notify potential victims, as does the European Union.
Just because companies are required to protect your information does not mean they are restricted from sharing it. In the US, companies can share your information without your explicit consent (see the following sidebar), though not all do so. Companies that collect PII are urged by the FTC to create a privacy policy and post it on their website. The State of California requires a privacy policy for any website that does business with a resident of the state (California Consumer Privacy Act (CCPA)).
While the privacy laws in the US seek to balance consumer protection with promoting commerce, privacy in the European Union is considered a fundamental right that outweighs the interests of commerce. This has led to much stricter privacy protection in the EU, but also makes commerce more difficult between the US and the EU.
Non-Obvious Relationship Awareness
Digital technologies have given people many new capabilities that simplify and expedite the collection of personal information. Every time a person comes into contact with digital technologies, information about that person is being made available. From location to web-surfing habits, your criminal record to your credit report, you are constantly being monitored. This information can then be aggregated to create profiles of each person. While much of the information collected was available in the past, collecting it and combining it took time and effort. Today, detailed information about a person is available for purchase from different companies. Even information not categorized as PII can be aggregated in such a way that an individual can be identified.
This process of collecting large quantities of a variety of information and then combining it to create profiles of individuals is known as Non-Obvious Relationship Awareness, or NORA. First commercialized by big casinos looking to find cheaters, NORA is used by both government agencies and private organizations, and it is big business.
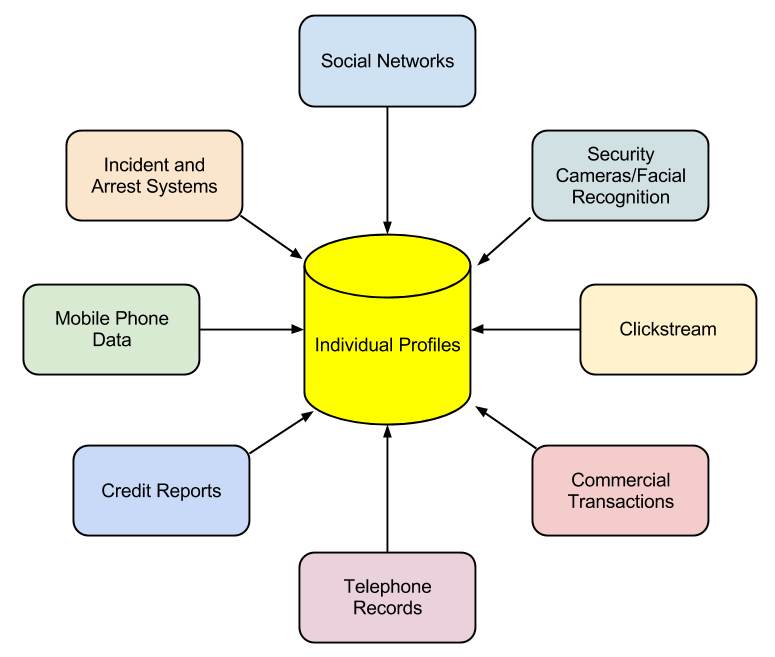
In some settings NORA can bring many benefits such as in law enforcement. By being able to identify potential criminals more quickly, crimes can be solved sooner or even prevented before they happen. But these advantages come at a price, namely, our privacy.
Restrictions on Data Collecting
In the United State the government has strict guidelines on how much information can be collected about its citizens. Certain classes of information have been restricted by laws over time and the advent of digital tools has made these restrictions more important than ever.
Children’s Online Privacy Protection Act
Websites that collect information from children under the age of thirteen are required to comply with the Children’s Online Privacy Protection Act (COPPA), which is enforced by the Federal Trade Commission (FTC). To comply with COPPA, organizations must make a good-faith effort to determine the age of those accessing their websites and, if users are under thirteen years old, must obtain parental consent before collecting any information.
Family Educational Rights and Privacy Act
The Family Educational Rights and Privacy Act (FERPA) is a US law that protects the privacy of student education records. In brief, this law specifies that parents have a right to their child’s educational information until the child reaches either the age of eighteen or begins attending school beyond the high school level. At that point control of the information is given to the child. While this law is not specifically about the digital collection of information on the Internet, the educational institutions that are collecting student information are at a higher risk for disclosing it improperly because of digital technologies.
Health Insurance Portability and Accountability Act
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) singles out records related to health care as a special class of personally identifiable information. This law gives patients specific rights to control their medical records, requires health care providers and others who maintain this information to get specific permission in order to share it, and imposes penalties on the institutions that breach this trust. Since much of this information is now shared via electronic medical records, the protection of those systems becomes paramount.
General Data Protection Regulation

The European Union, in an effort to help people take control over their personal data, passed the General Data Protection Regulation (GDPR) in May 2016. While this protection applies to the countries in the EU, it is having an impact of U.S. companies using the Internet as well. The regulation went into effect May 25, 2018.
EU and non-EU countries have different approaches to protecting the data of individuals. The focus in the U.S. has been on protecting data privacy so that it does not impact commercial interests.
In the EU the individual’s data privacy rights supercede those of business. Under GDPR data cannot be transferred to countries that do not have adequate data protection for individuals. Currently, those countries include, but are not limited to, the United States, Korea, and Japan. While the GDPR applies to countries in the EU, it is having an impact around the world as businesses in other countries seek to comply with this regulation. IEEE Spectrum.[11]
One week prior to the effective date of May 25, 2018, only 60% of companies surveyed reported they would be ready by the deadline.Information Management. Retrieved from https://www.information-management.com/opinion/playing-catch-up-with-the-general-data-protection-regulation.”[12]
Clearly, the message of GDPR has gone out around the world. It is likely that greater data protection regulations will forthcoming from the U.S. Congress as well.
Sidebar: Do Not Track
When it comes to getting permission to share personal information, the US and the EU have different approaches. In the US, the “opt-out” model is prevalent. In this model the default agreement states that you have agreed to share your information with the organization and must explicitly tell them that you do not want your information shared. There are no laws prohibiting the sharing of your data, beyond some specific categories of data such as medical records. In the European Union the “opt-in” model is required to be the default. In this case you must give your explicit permission before an organization can share your information.
To combat this sharing of information, the Do Not Track initiative was created. As its creators explain[13]:
Do Not Track is a technology and policy proposal that enables users to opt out of tracking by websites they do not visit, including analytics services, advertising networks, and social platforms. At present few of these third parties offer a reliable tracking opt out and tools for blocking them are neither user-friendly nor comprehensive. Much like the popular Do Not Call registry, Do Not Track provides users with a single, simple, persistent choice to opt out of third-party web tracking.

