6.3: Providing Resources in a Network
- Page ID
- 61653
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\( \newcommand{\id}{\mathrm{id}}\) \( \newcommand{\Span}{\mathrm{span}}\)
( \newcommand{\kernel}{\mathrm{null}\,}\) \( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\) \( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\) \( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\id}{\mathrm{id}}\)
\( \newcommand{\Span}{\mathrm{span}}\)
\( \newcommand{\kernel}{\mathrm{null}\,}\)
\( \newcommand{\range}{\mathrm{range}\,}\)
\( \newcommand{\RealPart}{\mathrm{Re}}\)
\( \newcommand{\ImaginaryPart}{\mathrm{Im}}\)
\( \newcommand{\Argument}{\mathrm{Arg}}\)
\( \newcommand{\norm}[1]{\| #1 \|}\)
\( \newcommand{\inner}[2]{\langle #1, #2 \rangle}\)
\( \newcommand{\Span}{\mathrm{span}}\) \( \newcommand{\AA}{\unicode[.8,0]{x212B}}\)
\( \newcommand{\vectorA}[1]{\vec{#1}} % arrow\)
\( \newcommand{\vectorAt}[1]{\vec{\text{#1}}} % arrow\)
\( \newcommand{\vectorB}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vectorC}[1]{\textbf{#1}} \)
\( \newcommand{\vectorD}[1]{\overrightarrow{#1}} \)
\( \newcommand{\vectorDt}[1]{\overrightarrow{\text{#1}}} \)
\( \newcommand{\vectE}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash{\mathbf {#1}}}} \)
\( \newcommand{\vecs}[1]{\overset { \scriptstyle \rightharpoonup} {\mathbf{#1}} } \)
\( \newcommand{\vecd}[1]{\overset{-\!-\!\rightharpoonup}{\vphantom{a}\smash {#1}}} \)
\(\newcommand{\avec}{\mathbf a}\) \(\newcommand{\bvec}{\mathbf b}\) \(\newcommand{\cvec}{\mathbf c}\) \(\newcommand{\dvec}{\mathbf d}\) \(\newcommand{\dtil}{\widetilde{\mathbf d}}\) \(\newcommand{\evec}{\mathbf e}\) \(\newcommand{\fvec}{\mathbf f}\) \(\newcommand{\nvec}{\mathbf n}\) \(\newcommand{\pvec}{\mathbf p}\) \(\newcommand{\qvec}{\mathbf q}\) \(\newcommand{\svec}{\mathbf s}\) \(\newcommand{\tvec}{\mathbf t}\) \(\newcommand{\uvec}{\mathbf u}\) \(\newcommand{\vvec}{\mathbf v}\) \(\newcommand{\wvec}{\mathbf w}\) \(\newcommand{\xvec}{\mathbf x}\) \(\newcommand{\yvec}{\mathbf y}\) \(\newcommand{\zvec}{\mathbf z}\) \(\newcommand{\rvec}{\mathbf r}\) \(\newcommand{\mvec}{\mathbf m}\) \(\newcommand{\zerovec}{\mathbf 0}\) \(\newcommand{\onevec}{\mathbf 1}\) \(\newcommand{\real}{\mathbb R}\) \(\newcommand{\twovec}[2]{\left[\begin{array}{r}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\ctwovec}[2]{\left[\begin{array}{c}#1 \\ #2 \end{array}\right]}\) \(\newcommand{\threevec}[3]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\cthreevec}[3]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \end{array}\right]}\) \(\newcommand{\fourvec}[4]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\cfourvec}[4]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \end{array}\right]}\) \(\newcommand{\fivevec}[5]{\left[\begin{array}{r}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\cfivevec}[5]{\left[\begin{array}{c}#1 \\ #2 \\ #3 \\ #4 \\ #5 \\ \end{array}\right]}\) \(\newcommand{\mattwo}[4]{\left[\begin{array}{rr}#1 \amp #2 \\ #3 \amp #4 \\ \end{array}\right]}\) \(\newcommand{\laspan}[1]{\text{Span}\{#1\}}\) \(\newcommand{\bcal}{\cal B}\) \(\newcommand{\ccal}{\cal C}\) \(\newcommand{\scal}{\cal S}\) \(\newcommand{\wcal}{\cal W}\) \(\newcommand{\ecal}{\cal E}\) \(\newcommand{\coords}[2]{\left\{#1\right\}_{#2}}\) \(\newcommand{\gray}[1]{\color{gray}{#1}}\) \(\newcommand{\lgray}[1]{\color{lightgray}{#1}}\) \(\newcommand{\rank}{\operatorname{rank}}\) \(\newcommand{\row}{\text{Row}}\) \(\newcommand{\col}{\text{Col}}\) \(\renewcommand{\row}{\text{Row}}\) \(\newcommand{\nul}{\text{Nul}}\) \(\newcommand{\var}{\text{Var}}\) \(\newcommand{\corr}{\text{corr}}\) \(\newcommand{\len}[1]{\left|#1\right|}\) \(\newcommand{\bbar}{\overline{\bvec}}\) \(\newcommand{\bhat}{\widehat{\bvec}}\) \(\newcommand{\bperp}{\bvec^\perp}\) \(\newcommand{\xhat}{\widehat{\xvec}}\) \(\newcommand{\vhat}{\widehat{\vvec}}\) \(\newcommand{\uhat}{\widehat{\uvec}}\) \(\newcommand{\what}{\widehat{\wvec}}\) \(\newcommand{\Sighat}{\widehat{\Sigma}}\) \(\newcommand{\lt}{<}\) \(\newcommand{\gt}{>}\) \(\newcommand{\amp}{&}\) \(\definecolor{fillinmathshade}{gray}{0.9}\)Networks of Many Sizes
Networks come in all sizes. They can go from basic networks consisting of two PCs to networks interfacing with many gadgets.
Basic networks introduced in homes empower sharing of assets, for example, printers, archives, pictures, and music between a couple of nearby PCs.
Worldwide internet users expect always to stay connected to the internet. They expect their connected devices to do the following:
- Stay connected to the internet to complete their work.
- Have the ability to send and receive data fast.
- Have the ability to send small and large quantities of data globally via any device connected to the internet.
Home office networks and small office networks are regularly set up by people who work from home or remote offices. They need to associate with a corporate network or other concentrated assets. Moreover, numerous independently employed business people utilize home office and little office networks to publicize and sell items, request supplies and speak with clients.
The Internet is the biggest network presently. Indeed, the term Internet implies a network of networks. The internet is the global worldwide network that connects millions of computers around the world. A computer can connect to another computer in a different country via the internet.
Clients and Servers
All PCs associated with a network are named hosts. Hosts are also called end devices.
Servers are PCs with programming that empower them to give data, similar to emails or website pages, to other network devices called clients. Each assistance requires separate server programming. For instance, a server requires web server programming to give web administrations to the network. A PC with server programming can offer types of assistance at the same time to one or numerous customers. Furthermore, a solitary PC can run numerous sorts of server programming. It might be vital for one PC to go about as a document server, a web server, and an email server in a home or private company.
Clients are PCs with programming introduced that empower them to ask for and show the server's data. A case of client programming is an internet browser, similar to Chrome or Firefox. A solitary PC can likewise run different kinds of custom programming. For instance, a client can browse email and view a site page while texting and tuning in to Internet radio.
Peer-to-Peer
Client and server programming ordinarily run on discrete PCs, yet it is also feasible for one PC to simultaneously complete the two jobs. In private companies and homes, hosts work as servers or clients on the network. This sort of system is known as a shared network. An example of that would be several users connected to the same printer from their individual devices.
Overview of Network Components
The link between the sender and the receiver can be as simple as a single cable connection between these two devices or more sophisticated as a set of switches and routers between them.

The network framework contains three classes of network segments:
- Devices
- Media
- Services
Devices and media are the physical components, or equipment, of the network. Equipment is regularly the noticeable segment of the network stage, for example, a PC, switch, remote passageway, or the cabling used to associate the devices.
Administrations incorporate a significant number of the basic network applications individuals utilize each day, similar to email facilitating administrations and web facilitating administrations. Procedures give the usefulness that coordinates and moves the messages through the network. Procedures are more subtle to us yet are basic to the activity of networks.
End Devices
An end device is either the source or destination of a message transmitted over the network. Each end device is identified by an IP address and a physical address. Both addresses are needed to communicate over a network. IP addresses are unique logical IP addresses that are assigned to every device within a network. If a device moves from one network to another, then the IP address has to be modified.
Physical addresses, also known as MAC (Media Access Control) addresses, are unique addresses assigned by the device manufacturers. These addresses are permanently burned into the hardware.
Intermediary Network Devices
Some devices act as intermediaries between devices. They are called delegated devices. These delegate devices give availability and guarantee that information streams over the network.
Routers utilize the destination end device address, related to data about the network interconnections, to decide how messages should take through the network.
Network Media
A medium called network media carries the act of transport data. The medium gives the channel over which the message makes a trip from source to destination.
Present-day organizations basically utilize three sorts of media to interconnect devices and give the pathway over which information can be transmitted.
These media are:
- Metallic wires within cables (Copper) - information is encoded into electrical driving forces.
- Glass or plastic fibers (fiber optic cable) - information is encoded as beats of light.
- Wireless transmission - information is encoded utilizing frequencies from the electromagnetic range.
Various sorts of network media have various highlights and advantages. Not all network media have similar qualities, nor are they all appropriate for the same purpose.


Bluetooth
While Bluetooth is not generally used to connect a device to the Internet, it is an important wireless technology that has enabled many functionalities that are used every day. When created in 1994 by Ericsson, it was intended to replace wired connections between devices. Today, it is the standard method for connecting nearby devices wirelessly. Bluetooth has a range of approximately 300 feet and consumes very little power, making it an excellent choice for various purposes.

Some applications of Bluetooth include: connecting a printer to a personal computer, connecting a mobile phone and headset, connecting a wireless keyboard and mouse to a computer, and connecting a remote for a presentation made on a personal computer.
Network Representations
To draw a diagram of a network, symbols are utilized by network professionals to represent the different devices and connections which make up a network.
A diagram gives a simple method to see how devices in a huge network are associated. This kind of "picture" of a network is known as a topology diagram. The capacity to perceive the legitimate portrayals of the physical systems administration segments is basic to have the option to imagine the association and activity of a network.
Notwithstanding these portrayals, particular phrasing is utilized while discussing how every one of these devices and media interfaces with one another. Significant terms to recall are:
- Network Interface Card: A NIC or LAN connector gives the physical association with the PC or opposite end device's network. The media that are associating the PC to the network administration device plug legitimately into the NIC.
- Physical Port: A connector or outlet on a network administration device where the media is associated with an end device or another network administration device.
- Interface: Specialized ports on a network administration device that associate with singular networks. Since switches are utilized to interconnect networks, the ports on a network allude to network interfaces.
Topology Diagrams
Understanding topology diagrams are required for anybody working with a network. They give a visual guide of how the network is associated.
There are two sorts of Topology diagrams:
- Physical topology and Logical topology diagrams. The physical topology diagrams identify the physical location of intermediary devices and cable installation.
- The Logical topology diagrams identify devices, addressing schemes, and ports.
With physical topology, it is quite self-explanatory. It is how they are interconnected with cables and wires physically. The logical topology is how connected devices are seen to the user.
Types of Networks
Networks foundations can fluctuate extraordinarily regarding:
- Size of the territory secured
- Number of users connected
- Number and kinds of administrations accessible
- Territory of obligation
The two most normal sorts of system frameworks:
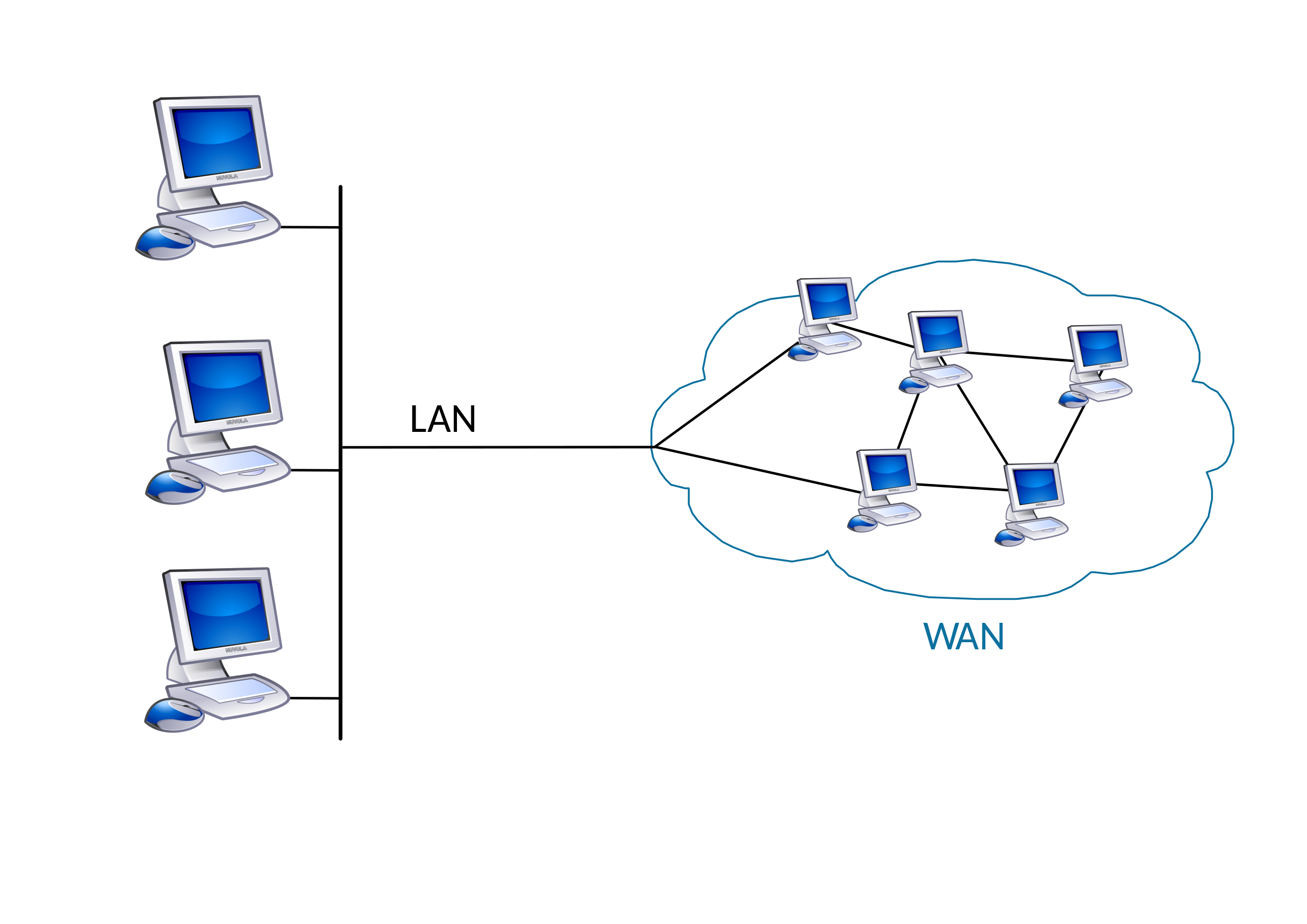
- Local Area Network (LAN): A network framework that gives access to clients and end devices in a little topographical zone, commonly an enterprise, small business, home, or small business network possessed and oversaw by an individual or IT department.
- Wide Area Network (WAN): A network foundation that gives access to different networks over a wide topographical region, commonly possessed and overseen by a broadcast communications specialist co-op.
Different kinds of networks include:
- Metropolitan Area Network (MAN): A network foundation that traverses a physical region bigger than a LAN yet littler than a WAN (e.g., a city). Keep an eye on are ordinarily worked by a solitary substance, for example, a huge association.
- Wireless LAN (WLAN): Like a LAN, it remotely interconnects clients and focuses on a little geological region.
- Storage Area Network (SAN): A network foundation intended to help record servers and give information stockpiling, recovery, and replication.
Local Area Networks
LANs are a network foundation that traverses a little topographical territory. Explicit highlights of LANs include:
- LANs interconnect end devices in a restricted region, for example, a home, school, place of business, or grounds.
- A solitary association or person normally directs a LAN. The managerial control that oversees the security and access control arrangements is upheld on the network level.
- LANs give rapid data transfer capacity to inward end gadgets and delegate devices.
 Figure \(\PageIndex{5}\): Local Area Network. Image by T.seppelt, derivative work from File:Ethernet.png, including content of the Open Clip Art Library, by © 2007 Nuno Pinheiro & David Vignoni & David Miller & Johann Ollivier Lapeyre & Kenneth Wimer & Riccardo Iaconelli / KDE / LGPL 3, User:George Shuklin and the Tango Project! is licensed CC BY-SA
Figure \(\PageIndex{5}\): Local Area Network. Image by T.seppelt, derivative work from File:Ethernet.png, including content of the Open Clip Art Library, by © 2007 Nuno Pinheiro & David Vignoni & David Miller & Johann Ollivier Lapeyre & Kenneth Wimer & Riccardo Iaconelli / KDE / LGPL 3, User:George Shuklin and the Tango Project! is licensed CC BY-SAWide Area Networks
WANs are a network foundation that traverses a wide topographical zone. WANs are ordinarily overseen by specialist organizations (SP) or Internet Service Providers (ISP).
Explicit highlights of WANs include:
- WANs interconnect LANs over wide geological zones, for example, between urban areas, states, territories, nations, or the mainland.
- Numerous specialist organizations typically manage WANs.
- WANs ordinarily give more slow speed joins between LANs
The Internet
The Internet is an overall assortment of interconnected networks (internetworks or web for short).
A portion of the LAN models is associated with one another through a WAN association. WANs are then associated with one another. The WAN association lines speak to all the assortments of ways we interface networks. WANs can connect through copper wires, fiber optic cables, and wireless transmissions.
No individual or group doesn't own the Internet. Guaranteeing compelling correspondence over this various framework requires the use of steady and generally perceived advances and norms, just as the collaboration of many network organization offices. Some associations have been produced to keep up the structure and normalization of Internet conventions and procedures. These organizations incorporate the Internet Engineering Task Force (IETF), Internet Corporation for Assigned Names and Numbers (ICANN), and the Internet Architecture Board (IAB), in addition to numerous others.
Have you ever wondered how your smartphone can function the way it does? Have you ever wondered how you can search for information on the web and find it within milliseconds? The world’s largest implementation of client/server computing and internetworking is the Internet.
The world’s largest implementation of client/server computing and internetworking is the Internet. The internet is also a system, which is the most extensive public way of communicating. The internet began in the 20th century; it initially started as a network for the U.S Department of Defense to globally connect university professors and scientists. Most small businesses and homes have access to the internet by subscribing to an internet service provider (ISP), a commercial organization with a permanent connection to the internet, which sells temporary connections to retail subscribers. For example, AT&T, NetZero, and T-Mobile. A DSL (Digital subscriber line) operates over existing telephone lines to carry data, voice, and video transmission rates. The base of the internet is TCP/IP networking protocol suite. When two users on the internet exchange messages, each message is decomposed into packets using the TCP/IP protocol.
Have you ever wondered what happens when you type a URL in the browser and press enter? The browser checks a DNS record in the cache to find the corresponding IP address to the domain. First, you type in a specific URL into your browser. The browser then checks the cache for a DNS record to find the website's corresponding IP address. If the URL is not in the cache, ISP’s (Internet Service Provider)’s DNS server starts a DNS query to find the server's IP address that hosts the website. The browser then starts a TCP connection with the server. Then, the browser sends an HTTP request to the webserver. After that, the server handles the request and sends an HTTP response back. Finally, the browser shows the HTML content. For example, www.Wikipedia.org/ has an IP address, that specific IP address could be searched starting with http:// on a browser/ The DNS contains a list of URLs, including their IP addresses.
The DNS (Domain Name System) changes domain names into IP addresses. The domain name is the English name of the thing, and that has 32-bits which are unique and numeric to that English name. To access a computer on the internet, they only need to specify the domain name.
Intranets and Extranets
There are two different terms which are like the term Internet: Intranets and Extranets.
Intranet is a term frequently used to describe a private association of LANs and WANs that has a place with an association. It is intended to be available only for approved individuals, workers, or others of an organization.
An extranet is a term used to describe the case when an organization wants to give secure and safe access to people who work for another organization yet expect access to the association's information. Examples of extranets include:
- An organization that is giving access to outside providers and temporary workers.
- An emergency clinic gives a booking system to specialists so they can make arrangements for their patients.
- A nearby office of training gives spending plans and staff data to the schools in its region.